Misc
简单编码
题目描述:
二八二八,咔咔就是发!
1 | 0122 110001 0153 0172 1010010 1000101 061 1011010 1010111 1101100 1100100 1001000 0122 0124 1001110 0105 0124 110000 064 1111010 0121 060 0144 1011010 1001101 1101100 1010010 0110 0124 1010110 1110000 1010101 1010010 060 1000110 0141 0126 0105 1101100 0117 1010101 1101100 1100100 1001000 0127 0126 0154 1010101 0124 0125 065 0123 0126 1000101 1100011 060 1001101 110000 0122 0110 0124 1010110 1110000 1010111 1010010 110000 110000 0171 1010110 0105 0144 1001110 1010101 1101100 1100100 1001000 0127 0126 1110000 0125 1010101 1010101 061 0141 1010101 110000 1100100 1001110 1010111 1101011 1010010 1001000 0124 0153 0112 0125 1010010 110000 1101011 0172 0122 0105 110001 0117 1010101 0154 0132 1001000 1010111 0124 1001010 0105 0124 1010101 065 1001011 1010110 1000101 0143 110000 1010111 1101100 1010010 0124 0124 0154 0112 0127 1010010 110000 060 0171 1010010 0105 1100100 0117 0125 1101100 0144 1001000 1010100 0124 0116 1000101 1010010 110000 110101 1010011 1010101 060 0144 1001110 1001110 1000110 0122 1001000 1010100 1101100 1110000 1011001 0124 0126 0105 111001 1010000 1010100 060 071 1010000 1010100 060 111101 |
二进制,八进制
写一个二进制,八进制转为字符串
exp:
1 | import re |
运行得到base编码
赛博厨子一把梭
最后flag为flag{77c34e530e3f2ffb6982f50939b3593b}
神秘的base
题目描述:
神奇密码在哪里
1 | EvAzEwo6E9RO4qSAHq42E9KvEv5zHDt34GtdHGJaHD7NHG42bwd= |
base换表爆破
1 | import base64 |
运行得到flag
最后flag为flag{8ee3021432edffaa57527461952e632c}
Stego
我应该去爱你
题目描述:
全世界还有谁,比我们能绝配~
下载附件,用AU打开文件,查看频谱
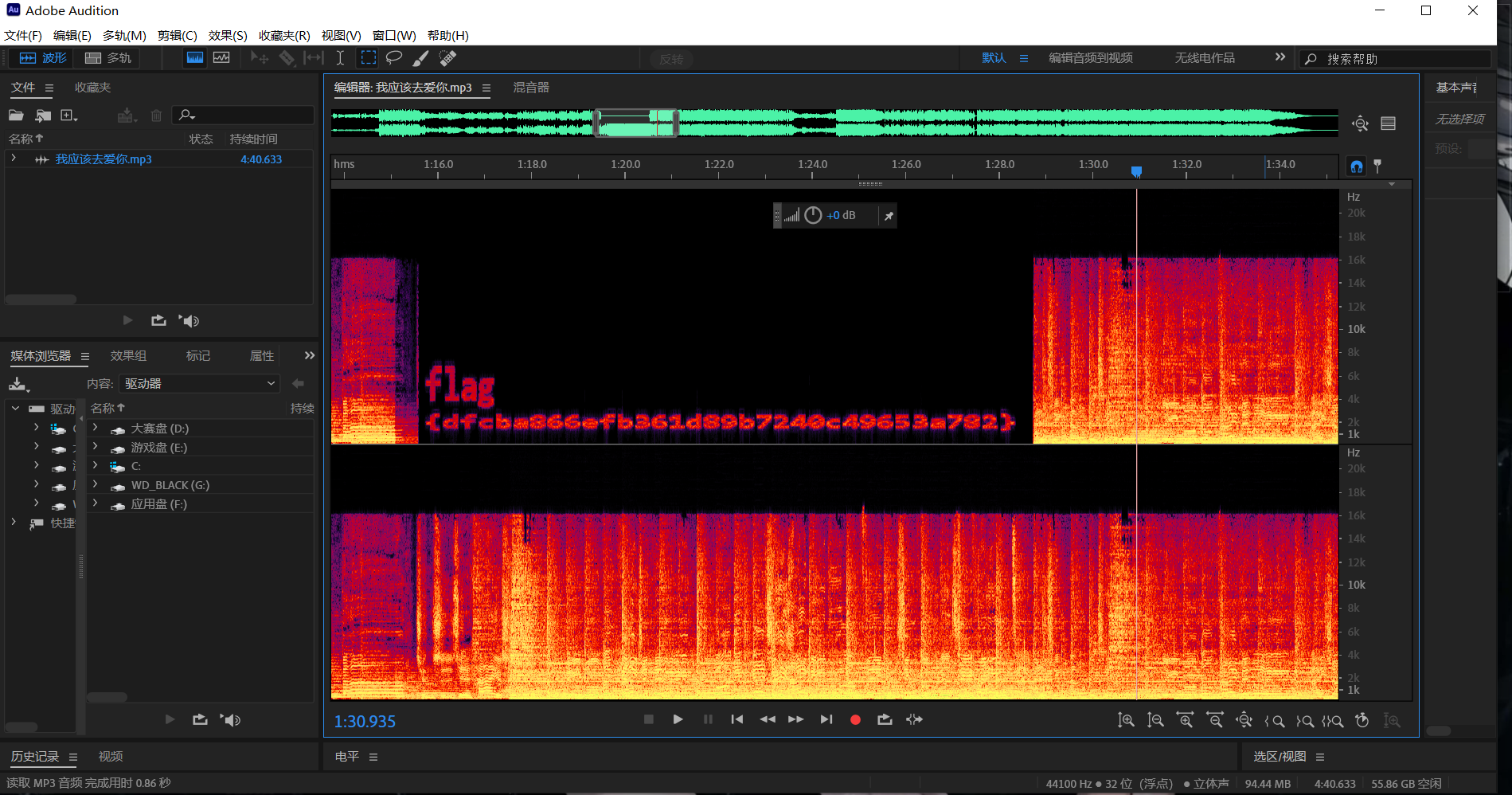
最后flag为flag{dfcba866efb361d89b7240c49653a782}
数独
题目描述:
闲来无事,做个数独吧(tips:将数独的结果横向排列,即可得到一组16位的神奇密码)
下载附件
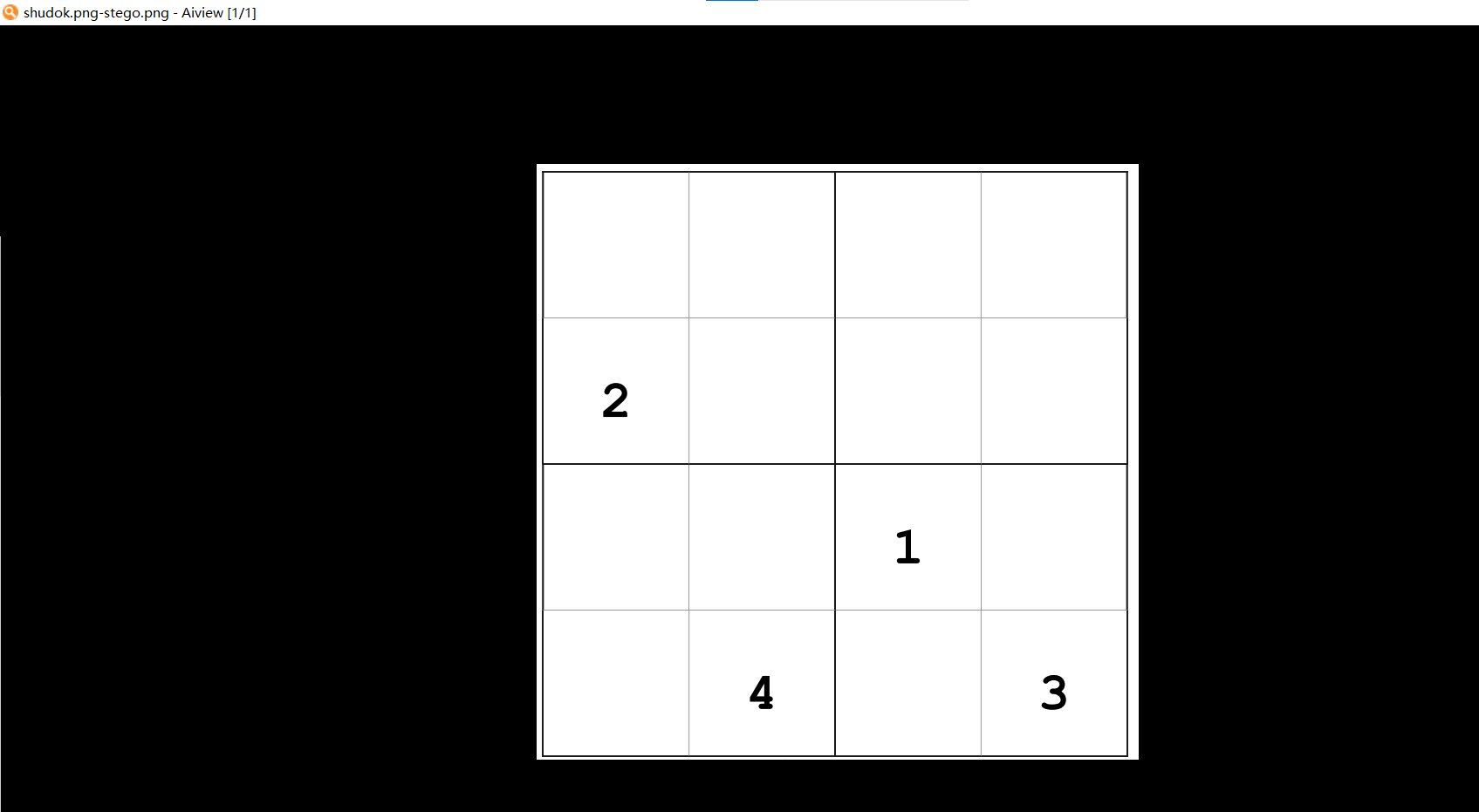
画图做数独
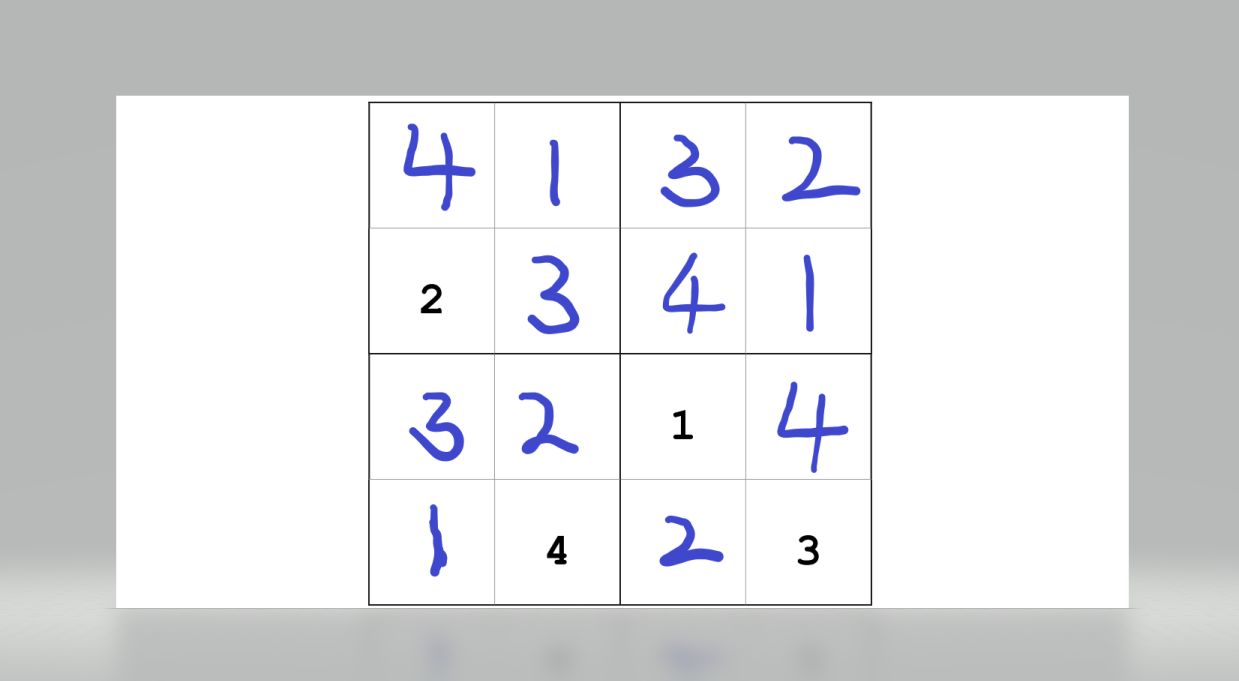
密码为4132234132141423
带密码的png隐写优先考虑cloacked-pixel
b神工具一把梭
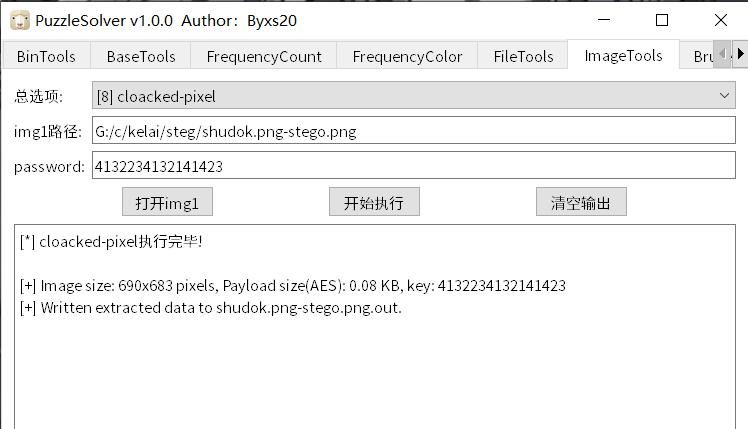
获得flag
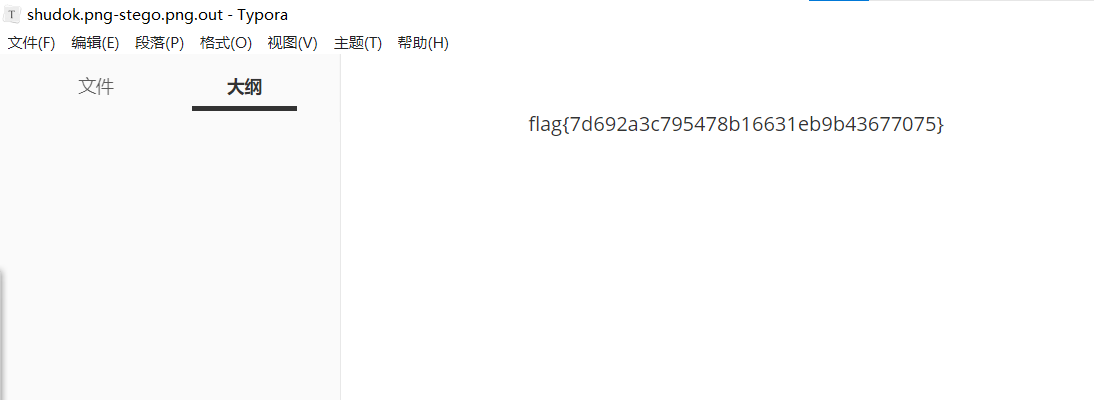
最后flag为flag{7d692a3c795478b16631eb9b43677075}
莫生气
题目描述:
他人生气我不气,气出病来无人替
下载附件

010查看文件
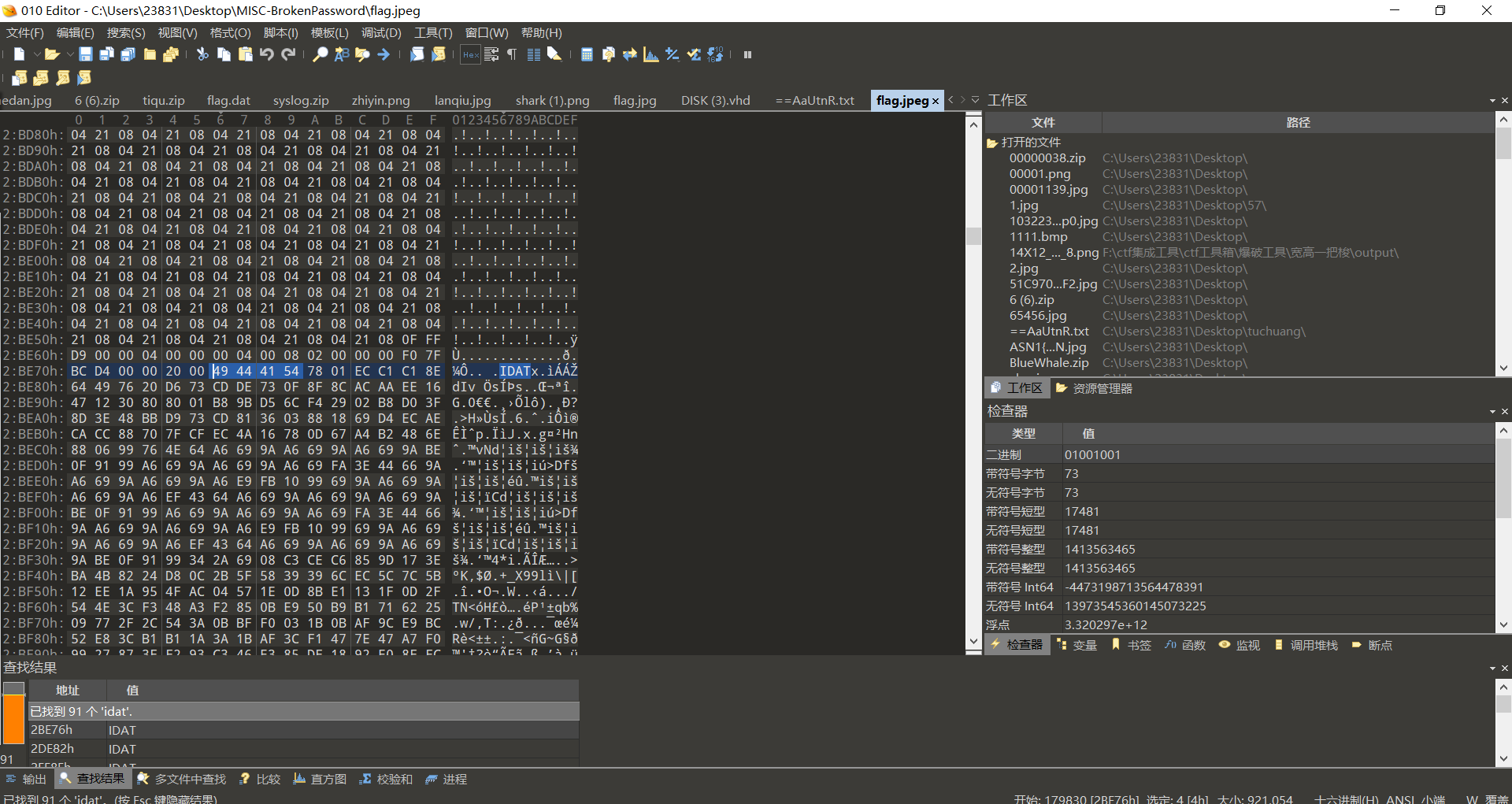
发现藏有png,缺少文件头,补全
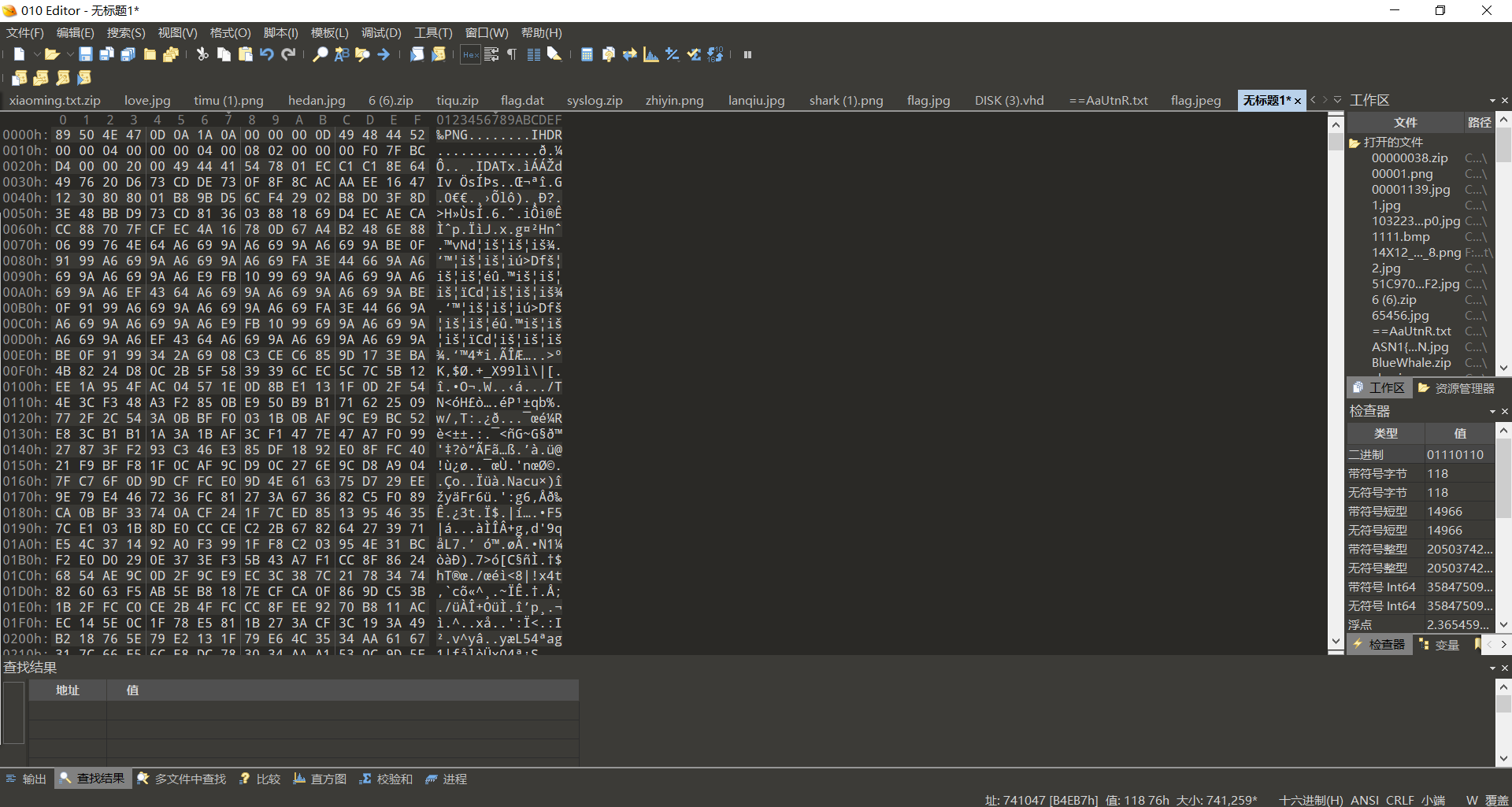
保存得到png文件
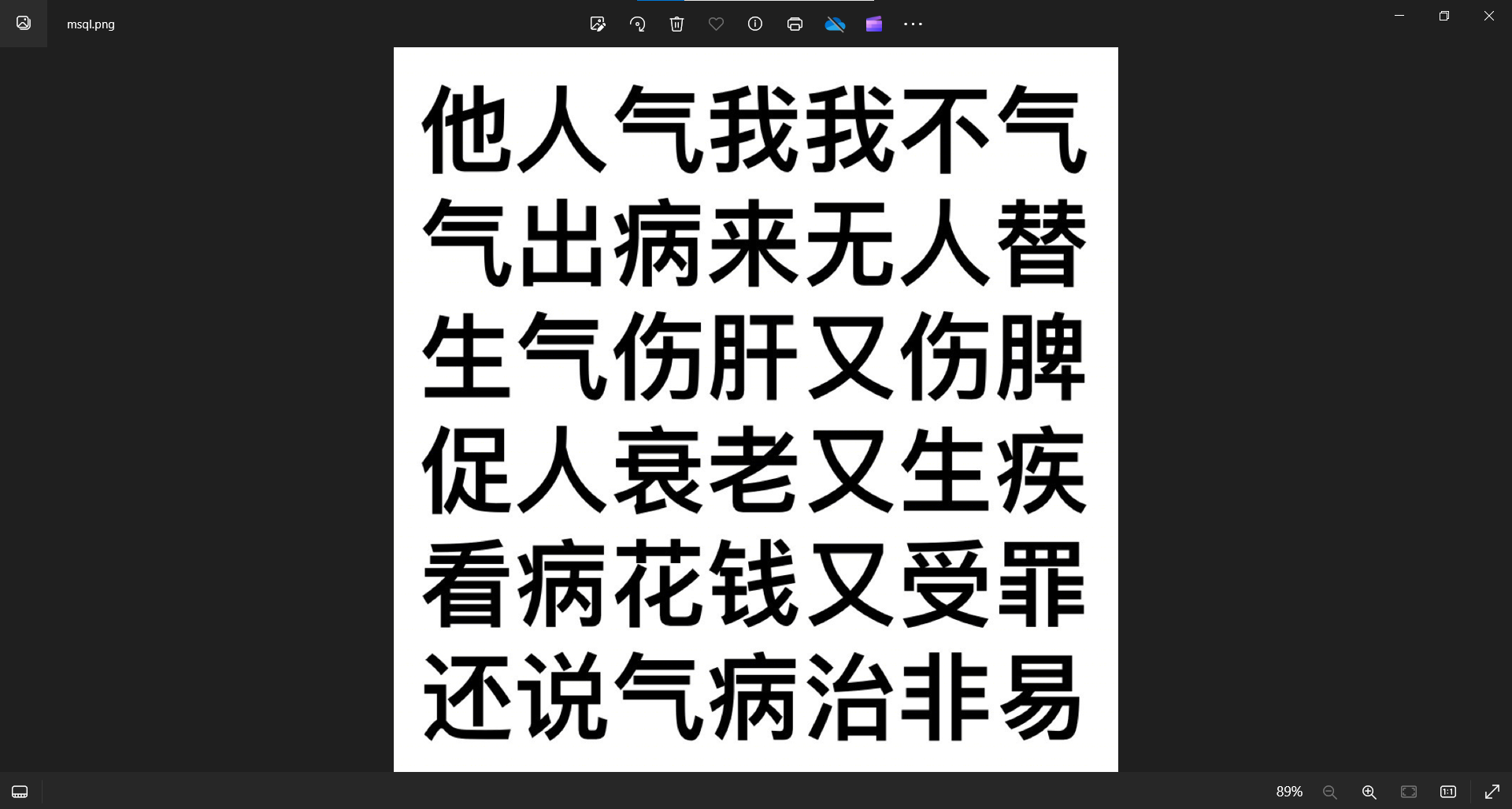
发现两张图都一样,猜测双图盲水印,b神工具一把梭
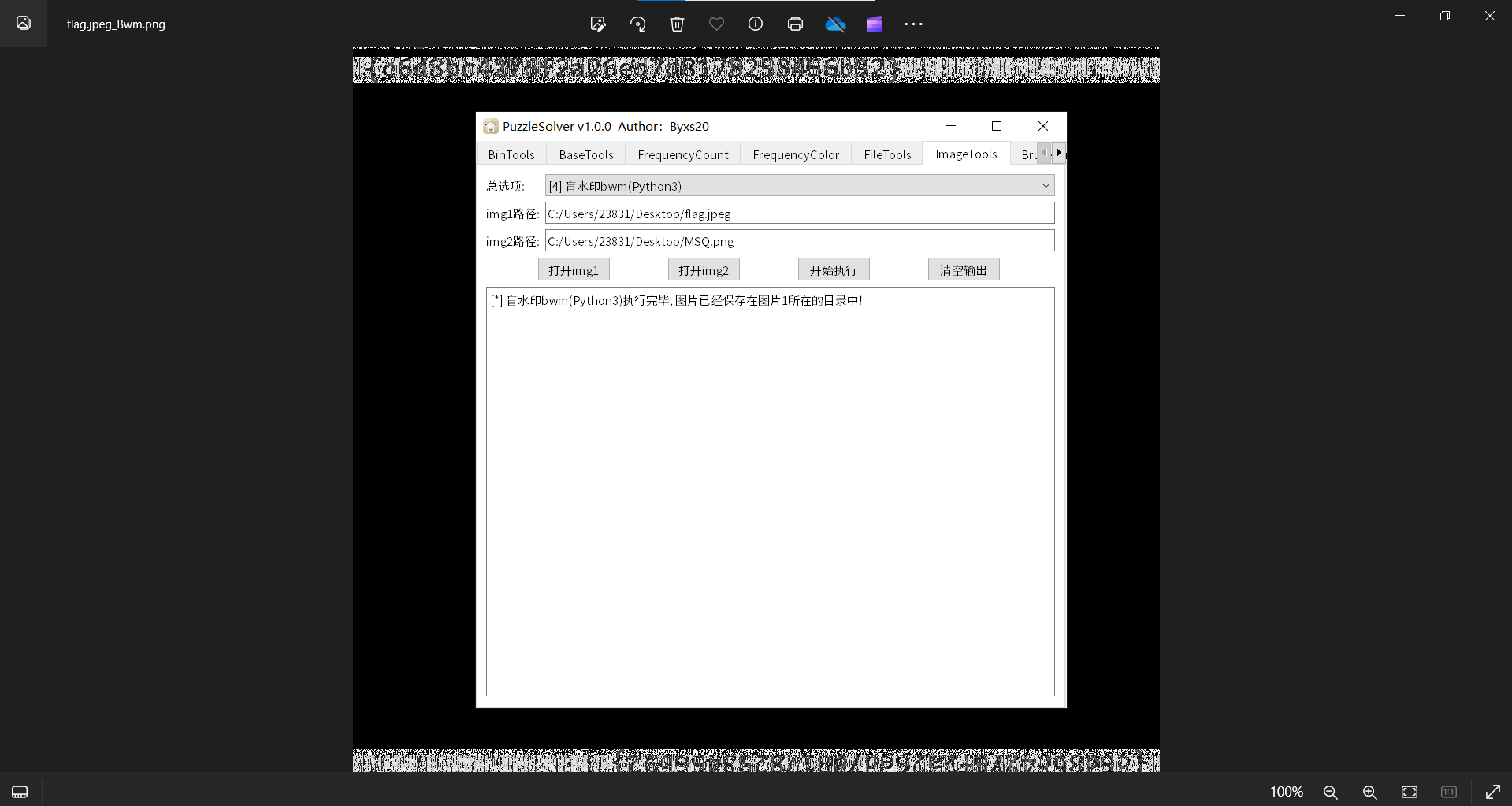
最后flag为flag{c6d8bc4276f2a26eo7d8178253456b92}
Forenisc
金刚大战哥斯拉
题目描述:
哥斯拉大战金刚,到底谁会获胜呢?
下载附件
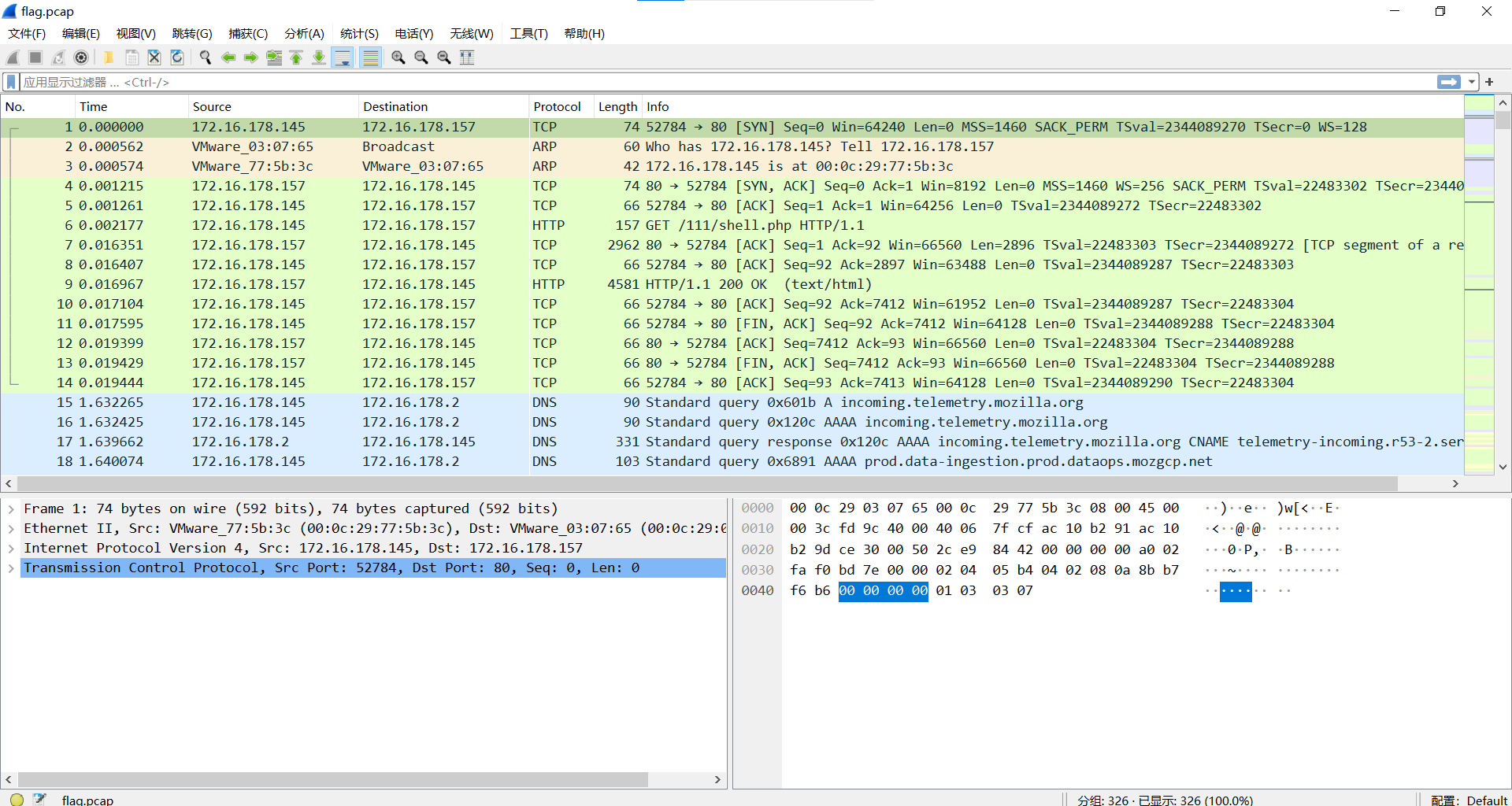
过滤http
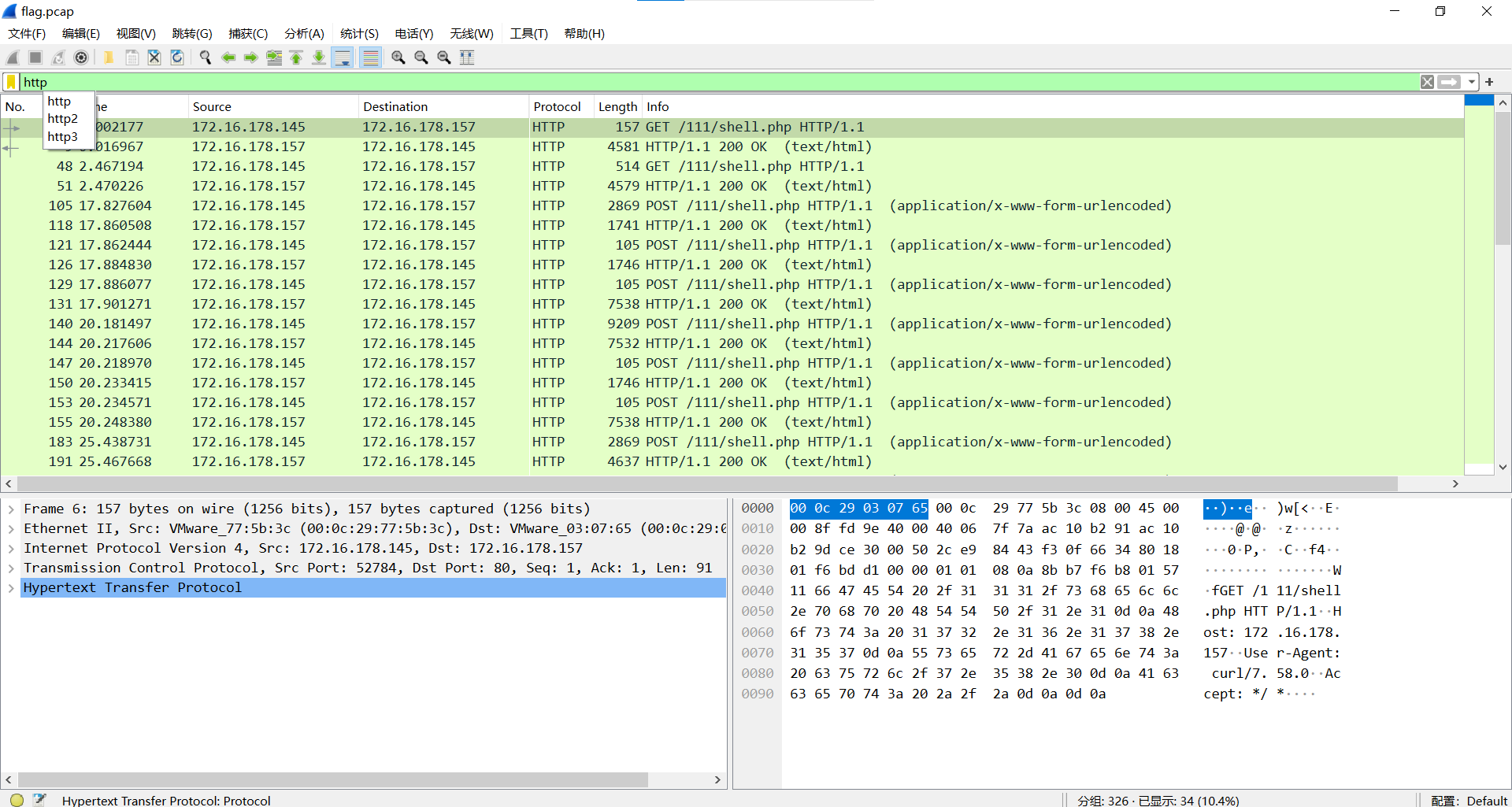
追踪流发现是哥斯拉流量(其实题目就告诉了)
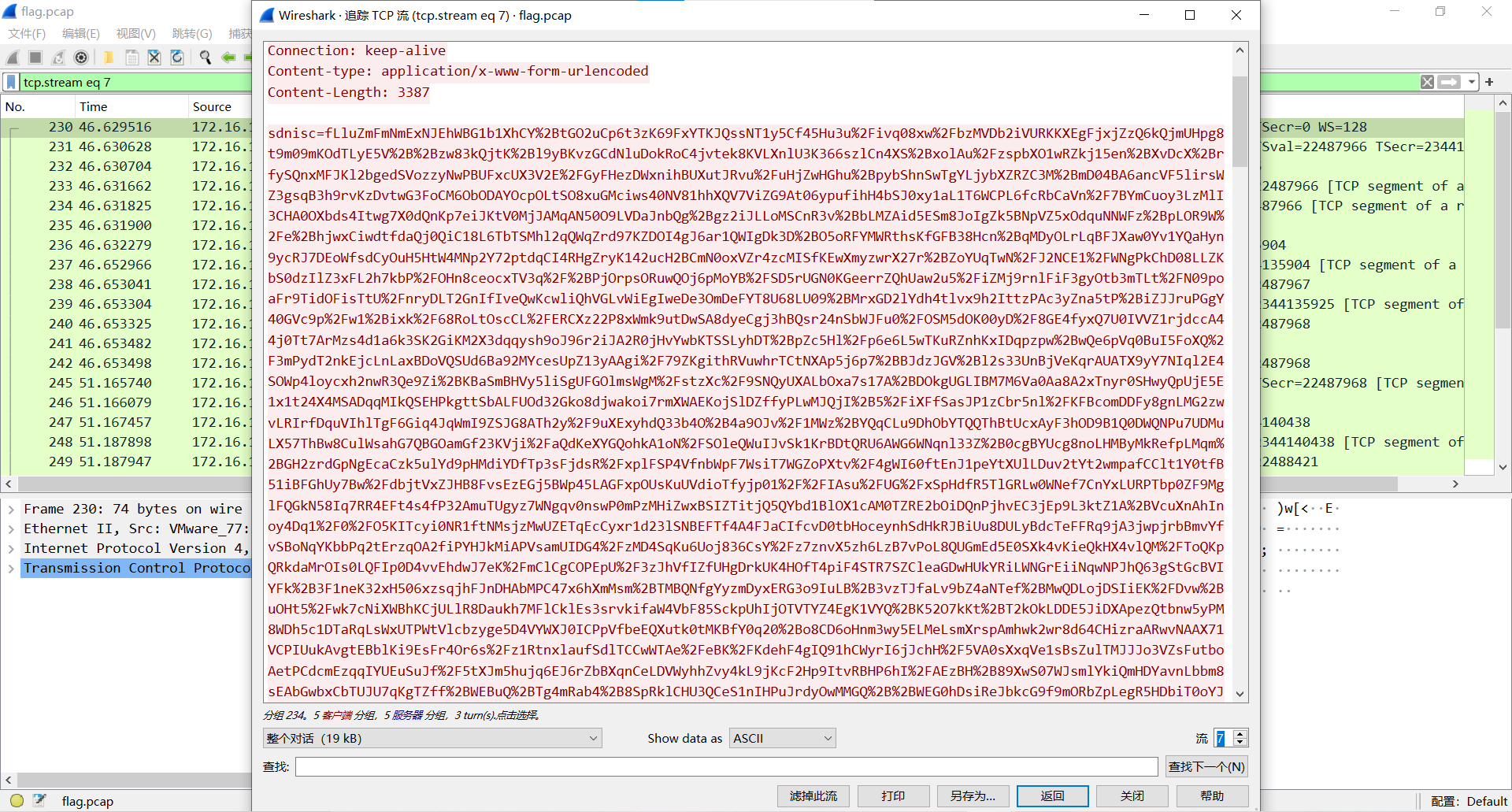
url解码得到哥斯拉流量密文
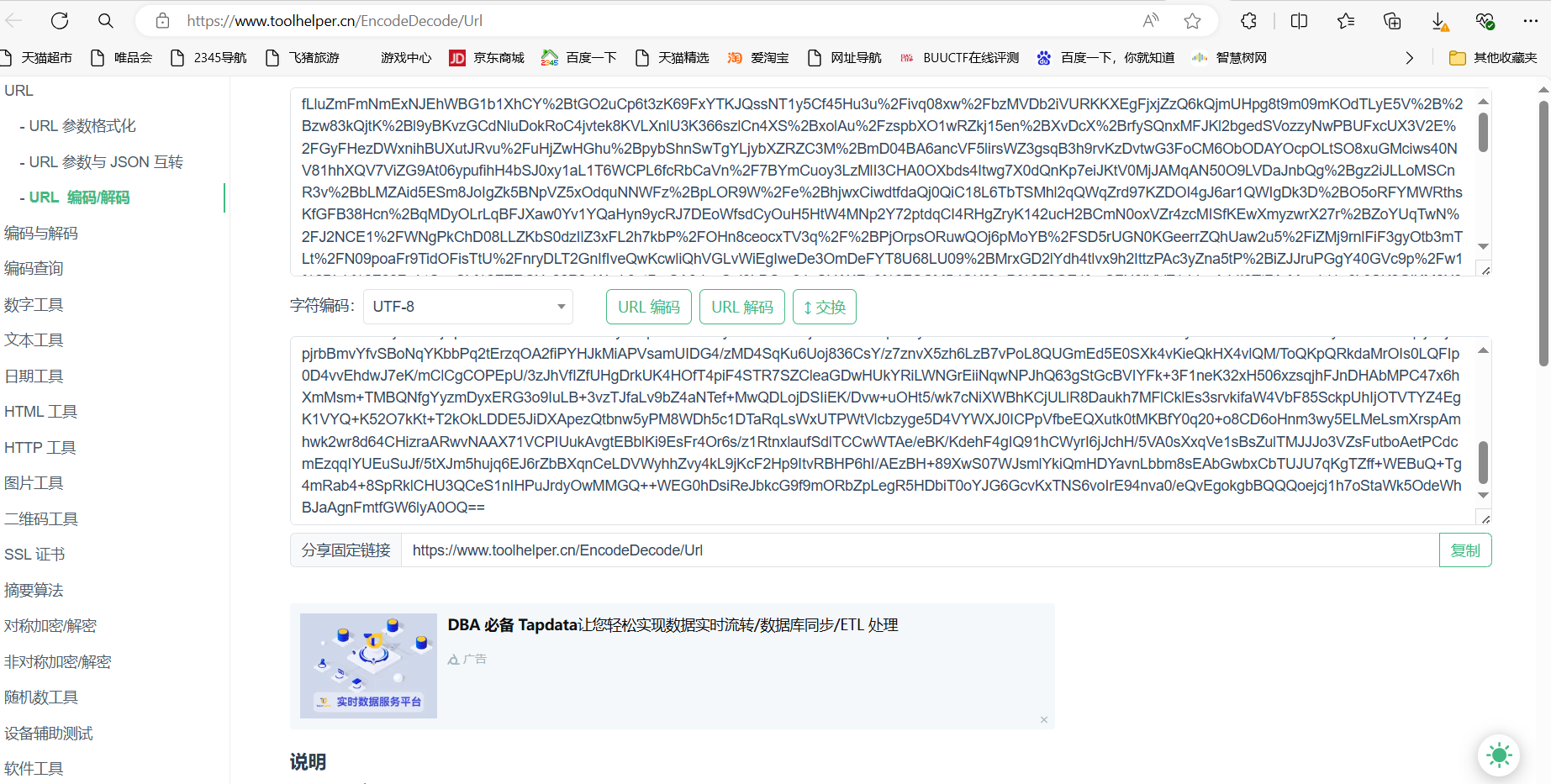
导出http对象
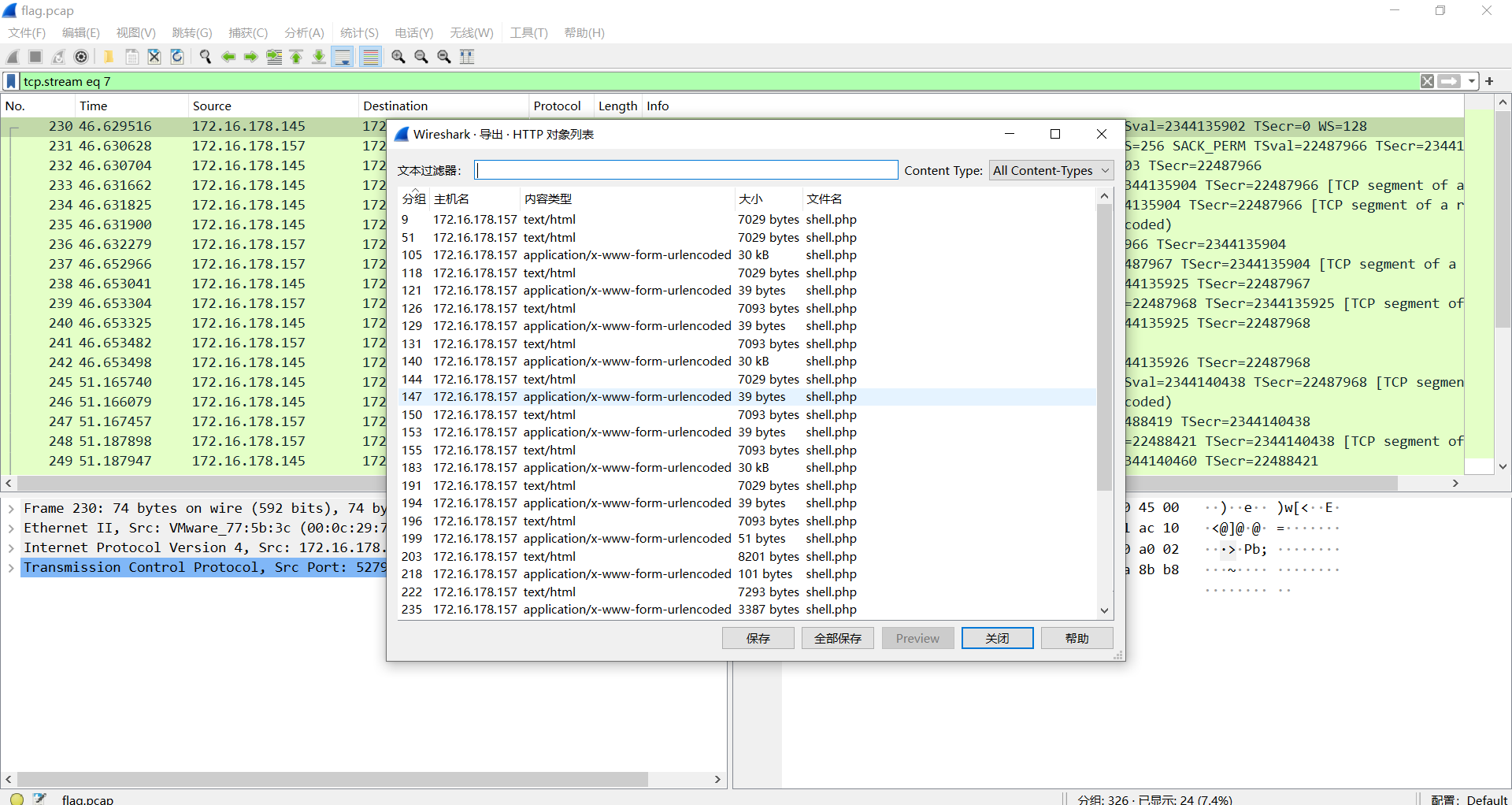
查看shell(1).php,发现哥斯拉流量的key
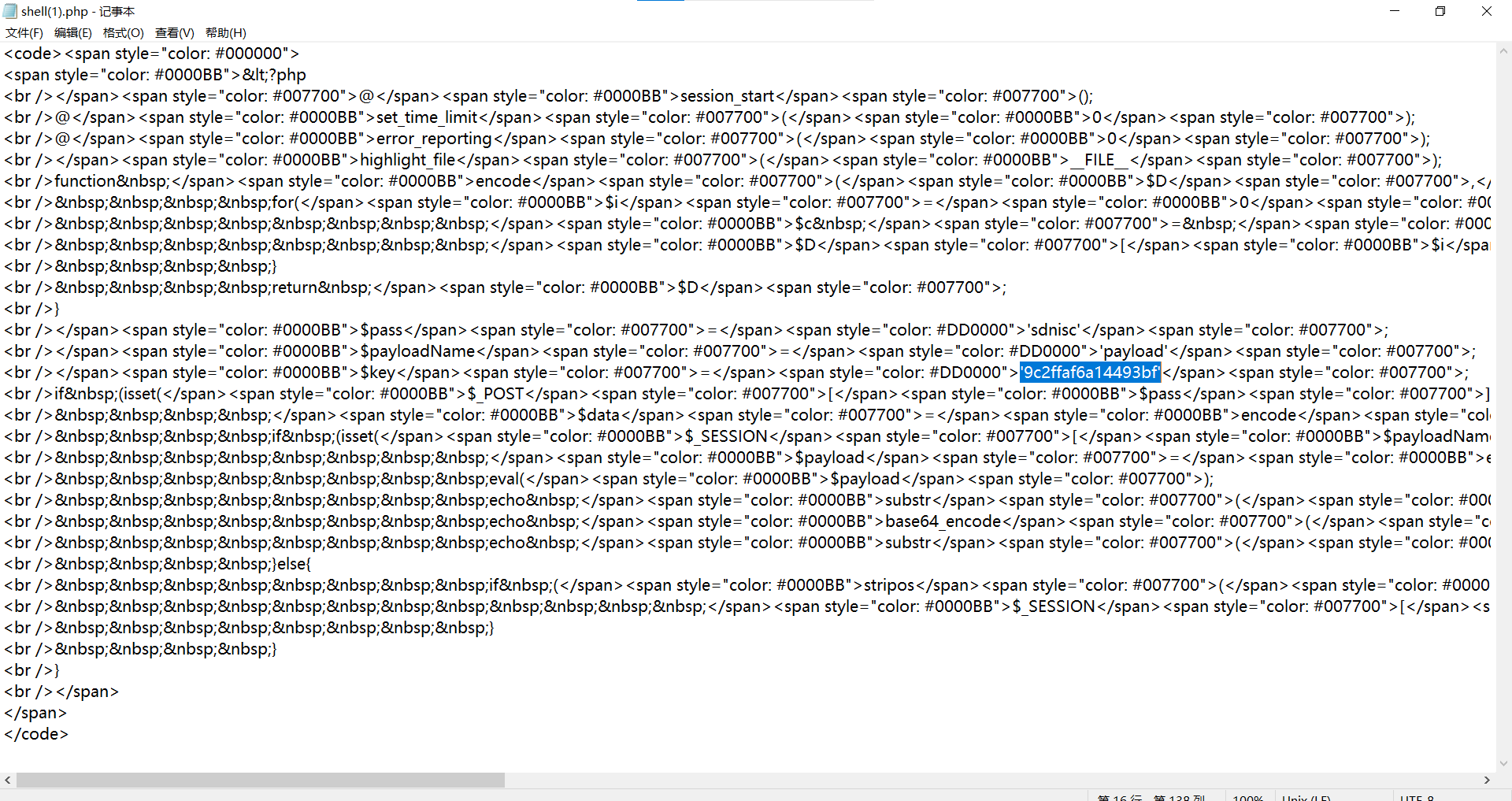
方法一:
哥斯拉流量解密exp:
1 | <?php |
运行得到
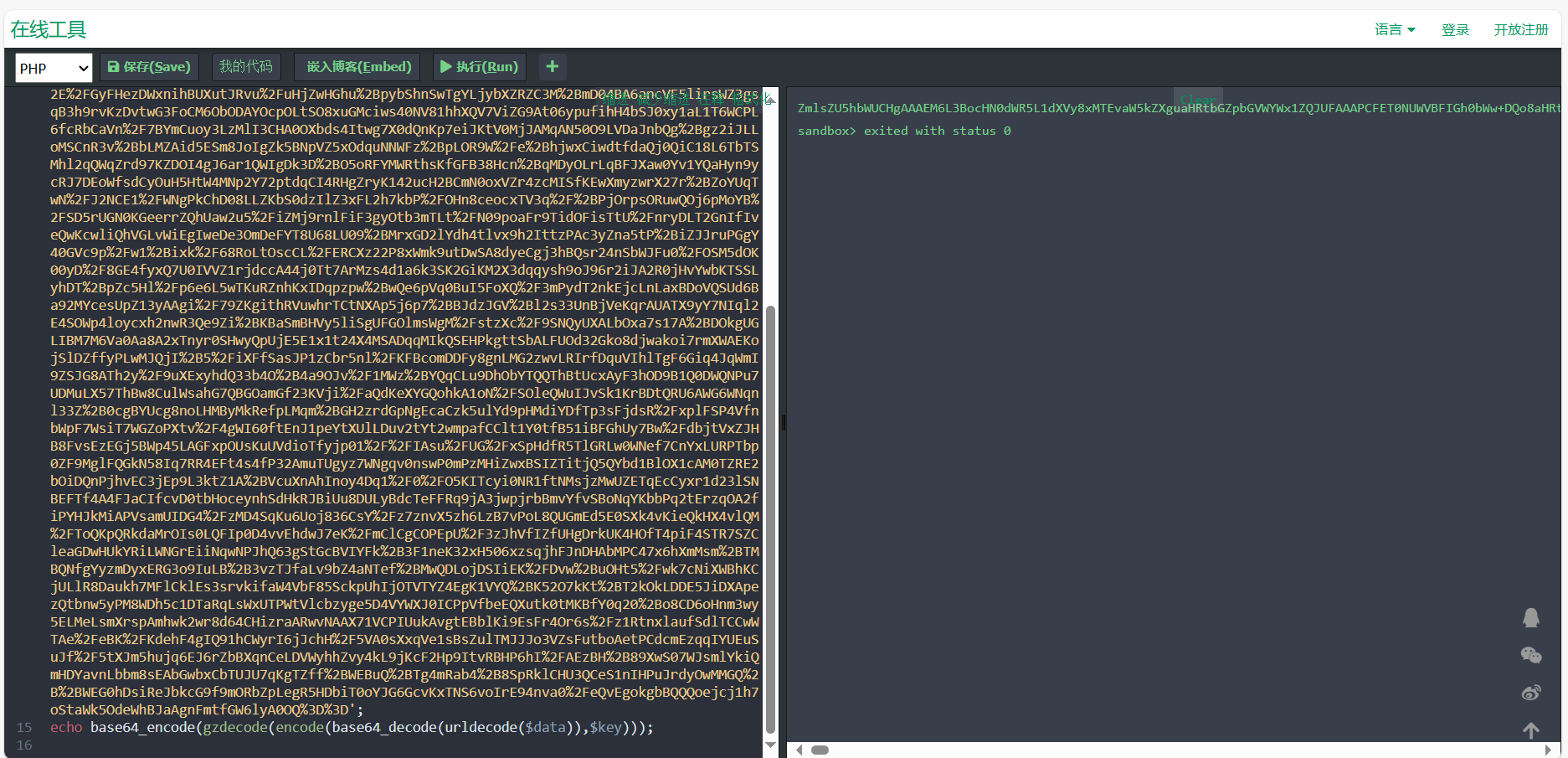
1 | ZmlsZU5hbWUCHgAAAEM6L3BocHN0dWR5L1dXVy8xMTEvaW5kZXguaHRtbGZpbGVWYWx1ZQJUFAAAPCFET0NUWVBFIGh0bWw+DQo8aHRtbCBsYW5nPSJlbiI+DQo8aGVhZD4NCiAgICA8bWV0YSBjaGFyc2V0PSJVVEYtOCI+DQogICAgPG1ldGEgbmFtZT0idmlld3BvcnQiIGNvbnRlbnQ9IndpZHRoPWRldmljZS13aWR0aCwgaW5pdGlhbC1zY2FsZT0xLjAiPg0KICAgIDxtZXRhIGh0dHAtZXF1aXY9IlgtVUEtQ29tcGF0aWJsZSIgY29udGVudD0iaWU9ZWRnZSI+DQogICAgPHRpdGxlPkRvY3VtZW50PC90aXRsZT4NCiAgICA8c3R5bGU+DQogICAgICAgICp7Ym94LXNpemluZzogYm9yZGVyLWJveDt9DQogICAgICAgIGJvZHl7DQogICAgICAgICAgICBiYWNrZ3JvdW5kOiAjMDAwOw0KICAgICAgICAgICAgbWFyZ2luOiAwOw0KICAgICAgICAgICAgcGFkZGluZzogMDsNCiAgICAgICAgICAgIG92ZXJmbG93OiBoaWRkZW47DQogICAgICAgICAgICB0ZXh0LXNoYWRvdzogMHB4IDBweCA4MHB4Ow0KICAgICAgICB9DQogICAgICAgIGgxew0KICAgICAgICAgICAgbWFyZ2luOiAwOw0KICAgICAgICAgICAgcGFkZGluZzogMDsNCiAgICAgICAgICAgIGNvbG9yOiAjMGZmOw0KICAgICAgICB9DQogICAgICAgIGF7Y29sb3I6ICNmZmY7fQ0KICAgICAgICAvKiDnm5LlrZDihpMgKi8NCiAgICAgICAgcHsNCiAgICAgICAgICAgIG1hcmdpbjogMDsNCiAgICAgICAgfQ0KICAgICAgICAuYm94ew0KICAgICAgICAgICAgLyog55uS5a2Q5a695bqm4oaTIC0tLeacgOWlveWIq+aUuSovDQogICAgICAgICAgICB3aWR0aDogNzAwcHg7DQogICAgICAgICAgICAvKiDorqnop4bpopHlsYXkuK3lr7npvZDihpMtLS3mnIDlpb3liKvliqggKi8NCiAgICAgICAgICAgIHRleHQtYWxpZ246IGNlbnRlcjsNCiAgICAgICAgICAgIC8qIGJvcmRlcjogMXB4IHNvbGlkICNmMDA7ICovDQogICAgICAgICAgICBjb2xvcjogI2ZmZjsNCiAgICAgICAgICAgIA0KICAgICAgICAgICAgcG9zaXRpb246IGFic29sdXRlOw0KICAgICAgICAgICAgbWFyZ2luOiAyMHB4IGF1dG8gMDsNCiAgICAgICAgICAgIHRvcDogMjBweDsNCiAgICAgICAgICAgIGxlZnQ6IDA7DQogICAgICAgICAgICByaWdodDogMDsNCiAgICAgICAgfQ0KICAgICAgICAvKiDlm77niYfmoLflvI/ihpMgKi8NCg0KICAgICAgICBpbWd7DQogICAgICAgICAgICAvKiDop4bpopHlrr3luqbihpMgLS0t5pyA5aW95LiN6KaB5aSn5LqO5LiK6Z2i55uS5a2Q55qE5a695bqmKi8NCiAgICAgICAgICAgIHdpZHRoOiA3MDBweDsNCiAgICAgICAgICAgIGhlaWdodDogMzkwcHg7DQogICAgICAgICAgICAvKiDngbDoibLnmoTmj4/ovrnihpMgLS0tcHjmmK/nspfnu4Ygc29saWTmmK/lrp7nur8gIzU1NeaYr+minOiJsuS7o+eggSDlj6/ku6Xnmb7luqZodG1s6aKc6Imy5Luj56CB5L+u5pS5Ki8NCiAgICAgICAgICAgIGJvcmRlcjogMnB4IHNvbGlkICMyMjI7DQogICAgICAgICAgICAvKiDlm77niYfnmoTlnIbop5IgKi8NCiAgICAgICAgICAgIGJvcmRlci1yYWRpdXM6IDVweDsNCiAgICAgICAgICAgIC8qIOWKqOeUu+aXtumXtCAqLw0KICAgICAgICAgICAgdHJhbnNpdGlvbjogMC44czsNCiAgICAgICAgfQ0KICAgICAgICAuaW1nMjpob3Zlcntib3JkZXI6IDJweCBzb2xpZCAjOTgwYjE4fQ0KDQogICAgICAgIC5ib3g+ZGl2ew0KICAgICAgICAgICAgcGFkZGluZzogMjBweDsNCiAgICAgICAgICAgIC8qIGJvcmRlcjogMXB4IHNvbGlkICNmMDA7ICovDQogICAgICAgIH0NCiAgICAgICAgLnN6ansNCiAgICAgICAgICAgIHBvc2l0aW9uOiBhYnNvbHV0ZTsNCiAgICAgICAgICAgIHRvcDogMDsNCiAgICAgICAgICAgIGxlZnQ6IDA7DQogICAgICAgICAgICBjb2xvcjogI2ZmZjsNCiAgICAgICAgICAgIHBhZGRpbmc6IDVweDsNCiAgICAgICAgICAgIGJvcmRlcjogMXB4IHNvbGlkICNlZWU7DQogICAgICAgICAgICBiYWNrZ3JvdW5kLWNvbG9yOiByZ2IoMCwwLDAsMC43KQ0KICAgICAgICB9DQogICAgICAgIC55bHsNCiAgICAgICAgICAgIGRpc3BsYXk6IGlubGluZTsNCiAgICAgICAgICAgIGJvcmRlci1ib3R0b206MXB4IGRvdHRlZCAjMGZmOw0KICAgICAgICB9DQogICAgICAgIC55bCBhew0KICAgICAgICAgICAgdGV4dC1kZWNvcmF0aW9uOiBub25lOw0KICAgICAgICAgICAgY29sb3I6I2M2ZDQ5MTsNCiAgICAgICAgICAgIA0KICAgICAgICB9DQogICAgICAgIC55bCBzcGFuew0KICAgICAgICAgICAgbWFyZ2luLXJpZ2h0OiA4cHg7DQogICAgICAgIH0NCiAgICA8L3N0eWxlPg0KPC9oZWFkPg0KPGJvZHk+DQogICAgPGNhbnZhcyBpZD0iY2FudmFzIj48L2NhbnZhcz4NCiAgICA8ZGl2IGNsYXNzPSJib3giPg0KICAgICAgICA8IS0tIOWbvueJh+mDqOWIhiAtLT4NCiAgICAgICAgPGltZyBjbGFzcz0iaW1nMiIgc3JjPSJodHRwczovL3RpbWdzYS5iYWlkdS5jb20vdGltZz9pbWFnZSZxdWFsaXR5PTgwJnNpemU9Yjk5OTlfMTAwMDAmc2VjPTE1Njg2NDE0NzImZGk9OWRiYWNiNzVjZjI0NWQwZWI1N2U3NTdlMGQyMjQ3ZjcmaW1ndHlwZT1qcGcmZXI9MSZzcmM9aHR0cCUzQSUyRiUyRmltZzEuZG91YmFuaW8uY29tJTJGdmlldyUyRnBob3RvJTJGbCUyRnB1YmxpYyUyRnAyMjkwMDU5MTU3LmpwZyIgYWx0PSIiPg0KICAgICAgICA8ZGl2IGNsYXNzPSJ0ZXh0Ij4NCiAgICAgICAgICAgIDxoMT7mn5Dmn5Dlronlhajnu4Q8L2gxPg0KDQogICAgICAgICAgICA8YnI+DQoNCiAgICAgICAgICAgIDxzcGFuIHN0eWxlPSJjb2xvcjogIzBmMCI+5a6Y5pa5Uee+pO+8mjwvc3Bhbj48c3Bhbj48YSB0YXJnZXQ9InZpZXdfd2luZG93IiBocmVmPSJodHRwczovL3d3dy5iYWlkdS5jb20vIj4xMjM0NTY8L2E+PC9zcGFuPg0KPGJyPjxicj4NCg0KICAgICAgICAgICAgPHAgY2xhc3M9Imdsb3ciIHN0eWxlPSJjb2xvcjogI2YwMDsgZm9udC1zaXplOjIxcHg7Ij7lj4vmg4Xmo4DmtYvvvIzor7flj4rml7bkv67lpI08L3A+DQogICAgICAgICAgICA8cCBjbGFzcz0iZ2xvdyIgc3R5bGU9ImNvbG9yOiAjZjAwOyBmb250LXNpemU6MTBweDsiPuaIluiBlOezu+acrOS6uuS/ruWkjTwvcD4NCiAgICAgICAgICAgIDxicj4NCiAgICAgICAgICAgIDxzcGFuIHN0eWxlPSJjb2xvcjogIzNlZTVkZiI+5p+Q5p+Q5p+QUXHvvJo8L3NwYW4+PHNwYW4+PGEgIHN0eWxlPSJjb2xvcjogI2U1NzQzZTsiIHRhcmdldD0idmlld193aW5kb3ciIGhyZWY9Imh0dHA6Ly93cGEucXEuY29tL21zZ3JkP3Y9MyZ1aW49Mjc2ODc3Njg5NSZzaXRlPXFxJm1lbnU9eWVzIj5mbGFnezIyN2FkMjQyZmM4MDEzYzhmZThmZjhmNDY3OTMzN2U0fTwvYT48L3NwYW4+DQogICAgICAgICAgICA8YnI+PGJyPg0KICAgICAgICAgICAgPFAgY2xhc3M9Imdsb3ciPuWuieWFqOS5i+i3r++8jOawuOS4jeWmpeWNjzwvUD4NCjxicj48YnI+PGJyPjxicj4NCiAgICAgICAgICAgIDxkaXYgY2xhc3M9InlsIj48c3BhbiBzdHlsZT0iY29sb3I6ICNmMGYiPuWPi+aDhemTvuaOpe+8mjwvc3Bhbj48c3Bhbj48YSBocmVmPSJodHRwczovL3d3dy5iYWlkdS5jb20vIj7mn5DnvZHnq5k8L2E+PC9zcGFuPiA8c3Bhbj48YSBocmVmPSJodHRwczovL3d3dy5iYWlkdS5jb20vIj7mn5DnvZHnq5k8L2E+PC9zcGFuPjxzcGFuPjxhIGhyZWY9Imh0dHBzOi8vd3d3LmJhaWR1LmNvbS8iPuafkOe9keermTwvYT48L3NwYW4+PC9kaXY+DQoNCiAgICAgICAgPC9kaXY+DQogICAgPC9kaXY+DQogICAgPGRpdiBjbGFzcz0ic3pqIj4NCjxwcmU+DQogIOWFpeS+teS4ieWtl+e7jw0KDQrov5vosLfmrYwg5om+5rOo5YWlDQoNCuayoeazqOWFpSDlsLHml4Hms6gNCg0K5rKh5peB5rOoIOeUqE9kYXkNCg0K5rKhT2RheSDnjJznm67lvZUNCg0K5rKh55uu5b2VIOWwseWXheaOog0KDQrniIbotKbmiLcg5om+5ZCO5Y+wDQoNCuS8oOWwj+mprCDmlL7lpKfpqawNCg0K5ou/5p2D6ZmQIOaMgumhtemdog0KDQo8L3ByZT4NCg0KICAgIA0KDQoNCiAgICA8IS0tIOmfs+S5kOmDqOWIhiAtLT4NCiAgICA8ZW1iZWQgaGVpZ2h0PSIwIiB3aWR0aD0iMCIgc3JjPSJodHRwczovL211c2ljLjE2My5jb20vb3V0Y2hhaW4vcGxheWVyP3R5cGU9MiZpZD0yOTQwMDkyNiZhdXRvPTEmaGVpZ2h0PTY2Ij48L2VtYmVkPg0KDQogICAgDQoNCg0KICAgIDwhLS0g5Lul5LiLanMgLS0+DQoNCg0KICAgIDxzY3JpcHQ+DQogICAgdmFyIGNhbnZhcyA9IGRvY3VtZW50LmdldEVsZW1lbnRCeUlkKCdjYW52YXMnKTsNCgkJdmFyIGN0eCA9IGNhbnZhcy5nZXRDb250ZXh0KCcyZCcpOw0KDQoNCgkJY2FudmFzLmhlaWdodCA9IHdpbmRvdy5pbm5lckhlaWdodDsNCgkJY2FudmFzLndpZHRoID0gd2luZG93LmlubmVyV2lkdGg7DQogICAgICAgIC8vIOS4i+mdoueahOmbt+WGm+WwseaYr+S7o+eggembqOeahOaWh+Wtlw0KCQl2YXIgdGV4dHMgPSAn6Zu35YabJy5zcGxpdCgnJyk7DQoNCgkJdmFyIGZvbnRTaXplID0gMTY7DQoJCXZhciBjb2x1bW5zID0gY2FudmFzLndpZHRoL2ZvbnRTaXplOw0KCQkvLyDnlKjkuo7orqHnrpfovpPlh7rmloflrZfml7blnZDmoIfvvIzmiYDku6Xplb/luqbljbPkuLrliJfmlbANCgkJdmFyIGRyb3BzID0gW107DQoJCS8v5Yid5aeL5YC8DQoJCWZvcih2YXIgeCA9IDA7IHggPCBjb2x1bW5zOyB4Kyspew0KCQkJZHJvcHNbeF0gPSAxOw0KCQl9DQoNCgkJZnVuY3Rpb24gZHJhdygpew0KCQkJLy/orqnog4zmma/pgJDmuJDnlLHpgI/mmI7liLDkuI3pgI/mmI4NCgkJCWN0eC5maWxsU3R5bGUgPSAncmdiYSgwLCAwLCAwLCAwLjA1KSc7DQoJCQljdHguZmlsbFJlY3QoMCwgMCwgY2FudmFzLndpZHRoLCBjYW52YXMuaGVpZ2h0KTsNCgkJCS8v5paH5a2X6aKc6ImyDQoJCQljdHguZmlsbFN0eWxlID0gJyMwRjAnOw0KCQkJY3R4LmZvbnQgPSBmb250U2l6ZSArICdweCBhcmlhbCc7DQoJCQkvL+mAkOihjOi+k+WHuuaWh+Wtlw0KCQkJZm9yKHZhciBpID0gMDsgaSA8IGRyb3BzLmxlbmd0aDsgaSsrKXsNCgkJCQl2YXIgdGV4dCA9IHRleHRzW01hdGguZmxvb3IoTWF0aC5yYW5kb20oKSp0ZXh0cy5sZW5ndGgpXTsNCgkJCQljdHguZmlsbFRleHQodGV4dCwgaSpmb250U2l6ZSwgZHJvcHNbaV0qZm9udFNpemUpOw0KDQoJCQkJaWYoZHJvcHNbaV0qZm9udFNpemUgPiBjYW52YXMuaGVpZ2h0IHx8IE1hdGgucmFuZG9tKCkgPiAwLjk1KXsNCgkJCQkJZHJvcHNbaV0gPSAwOw0KCQkJCX0NCg0KCQkJCWRyb3BzW2ldKys7DQoJCQl9DQoJCX0NCglzZXRJbnRlcnZhbChkcmF3LCAzMyk7DQo8L3NjcmlwdD4NCjwvYm9keT4NCjwvaHRtbD5tZXRob2ROYW1lAgoAAAB1cGxvYWRGaWxl |
base解码得到flag
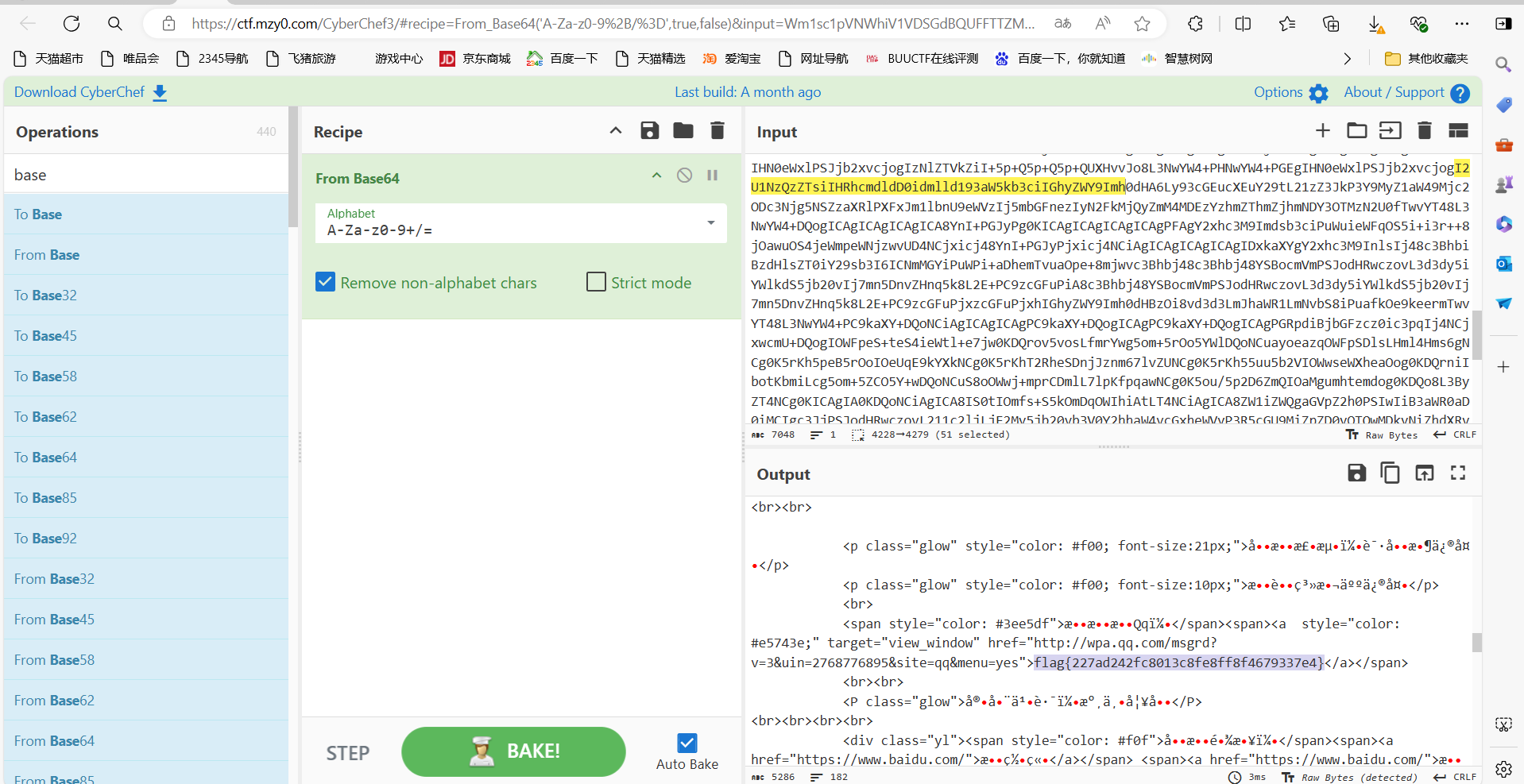
方法二:
流量一把梭
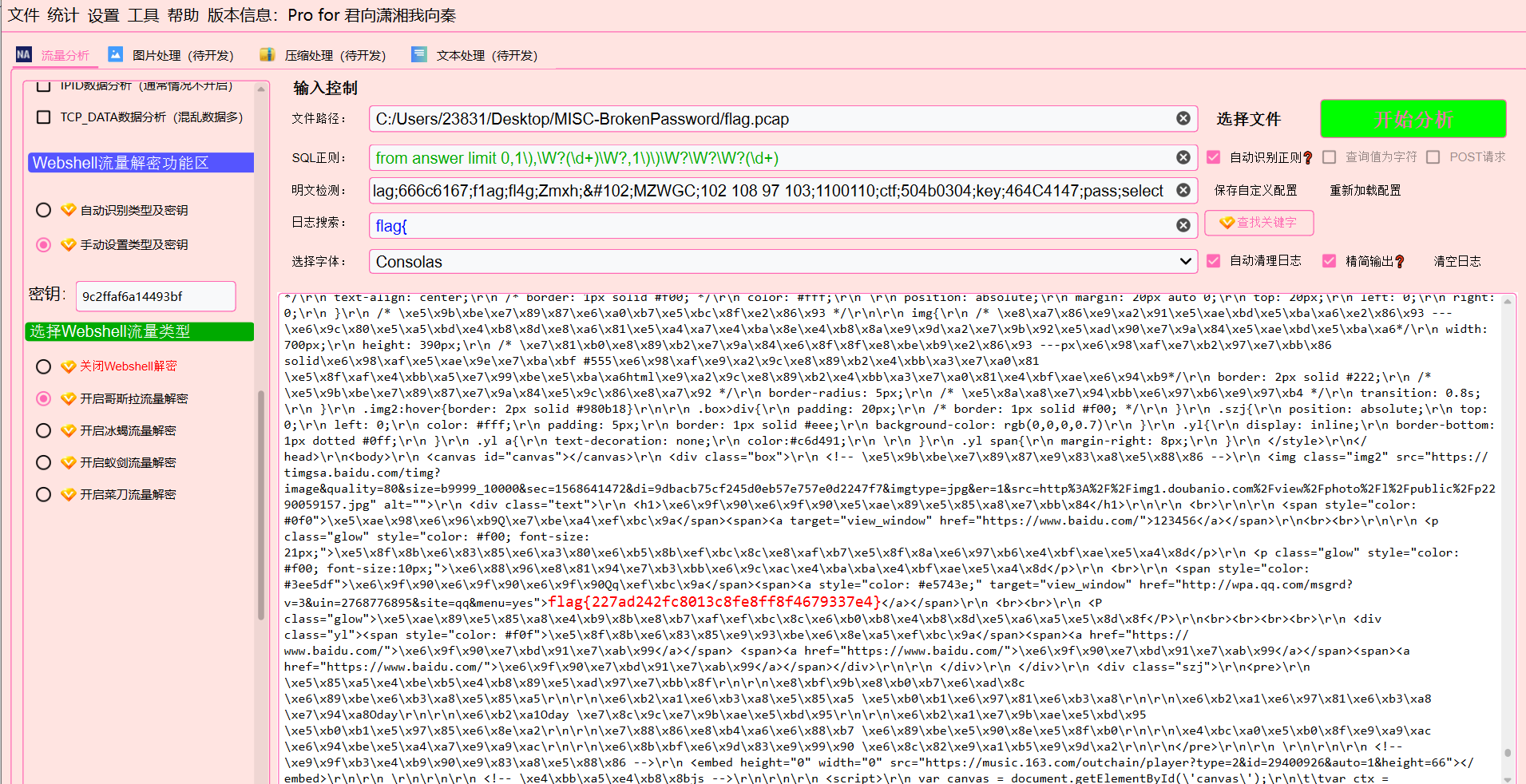
最后flag为flag{227ad242fc8013c8fe8ff8f4679337e4}
啊吧啊吧的数据包
题目描述:
一打开数据包我就,啊吧啊吧啊吧。
下载附件
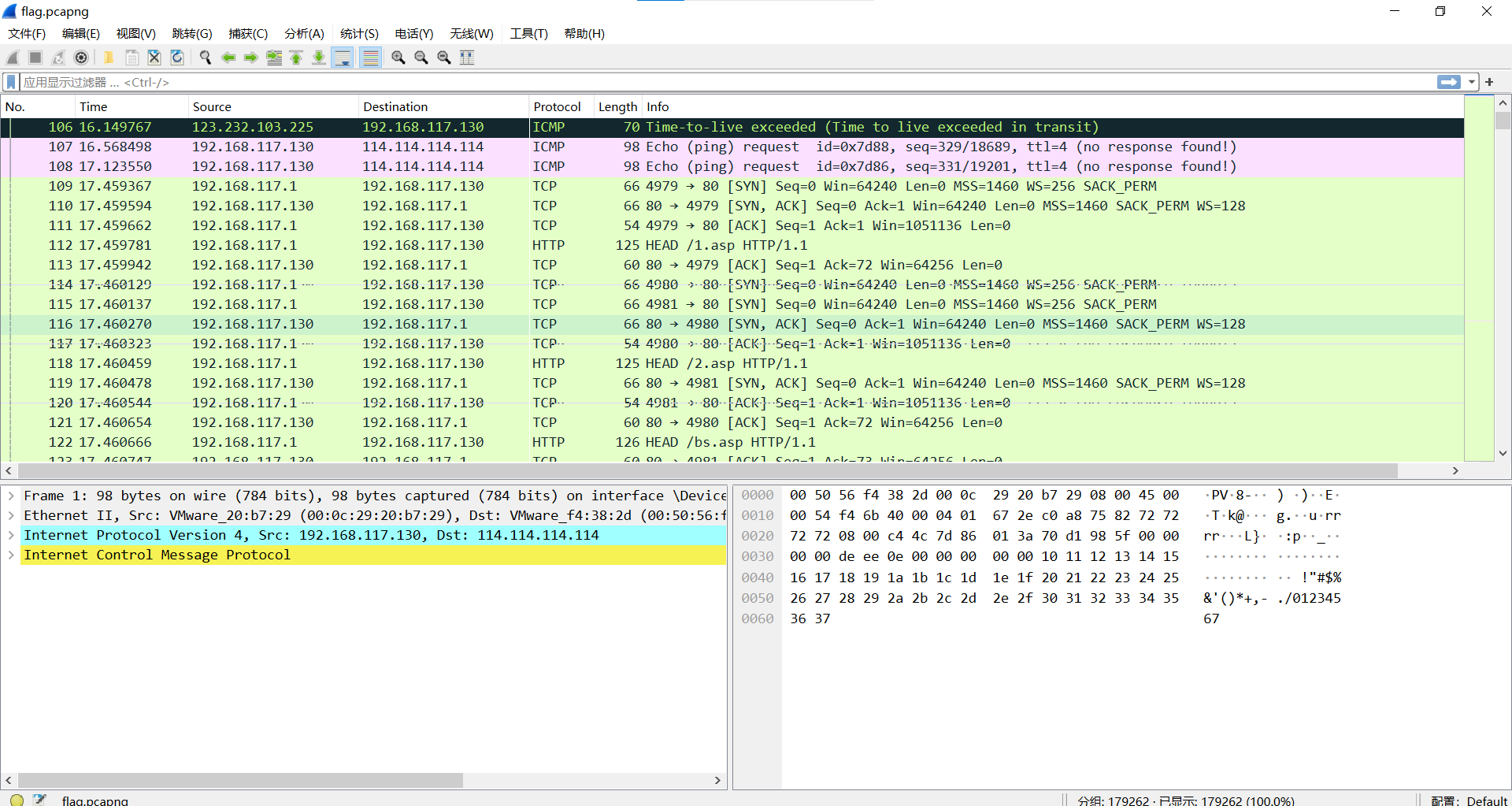
过滤http
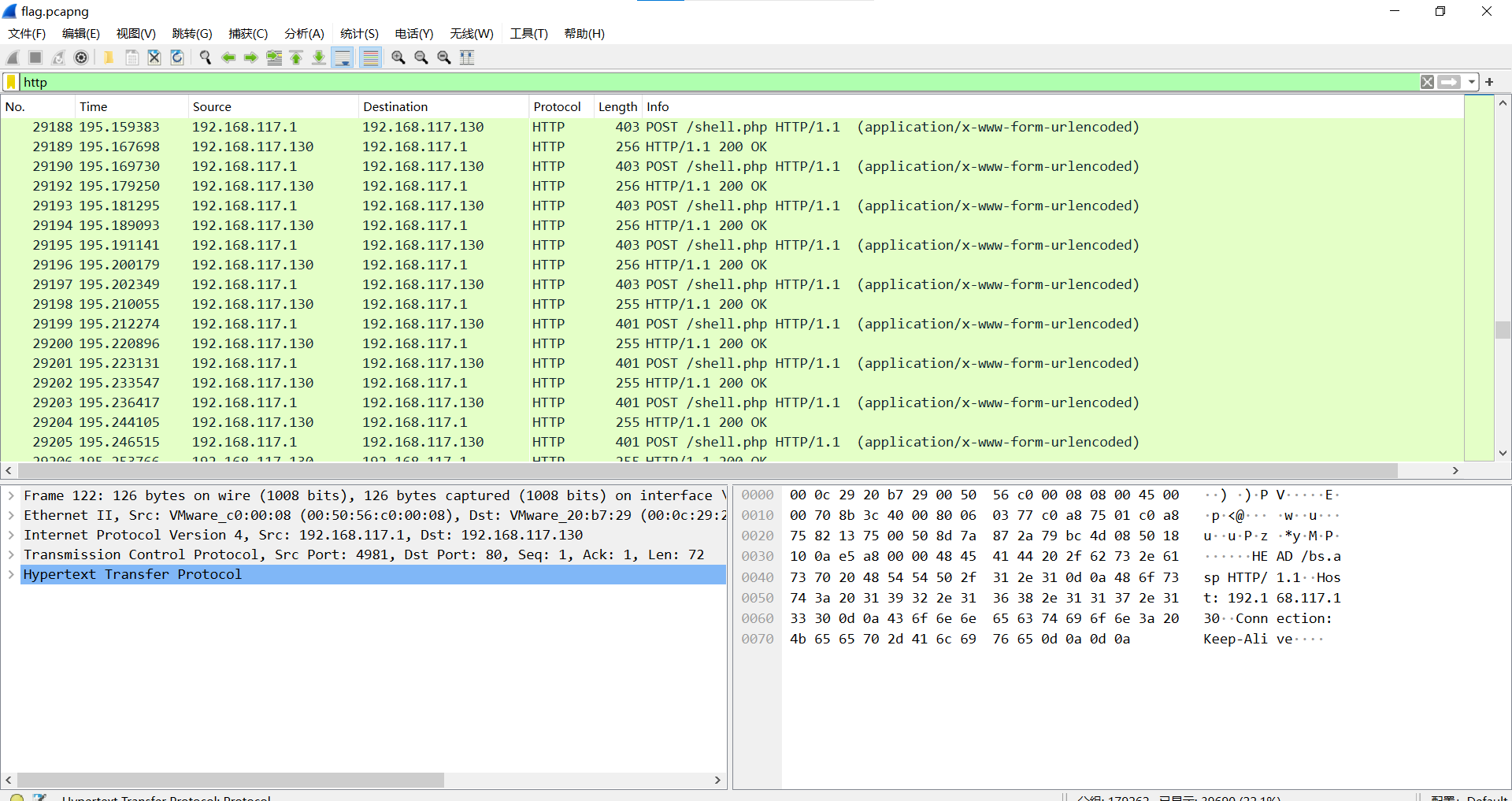
http.request.method == POST
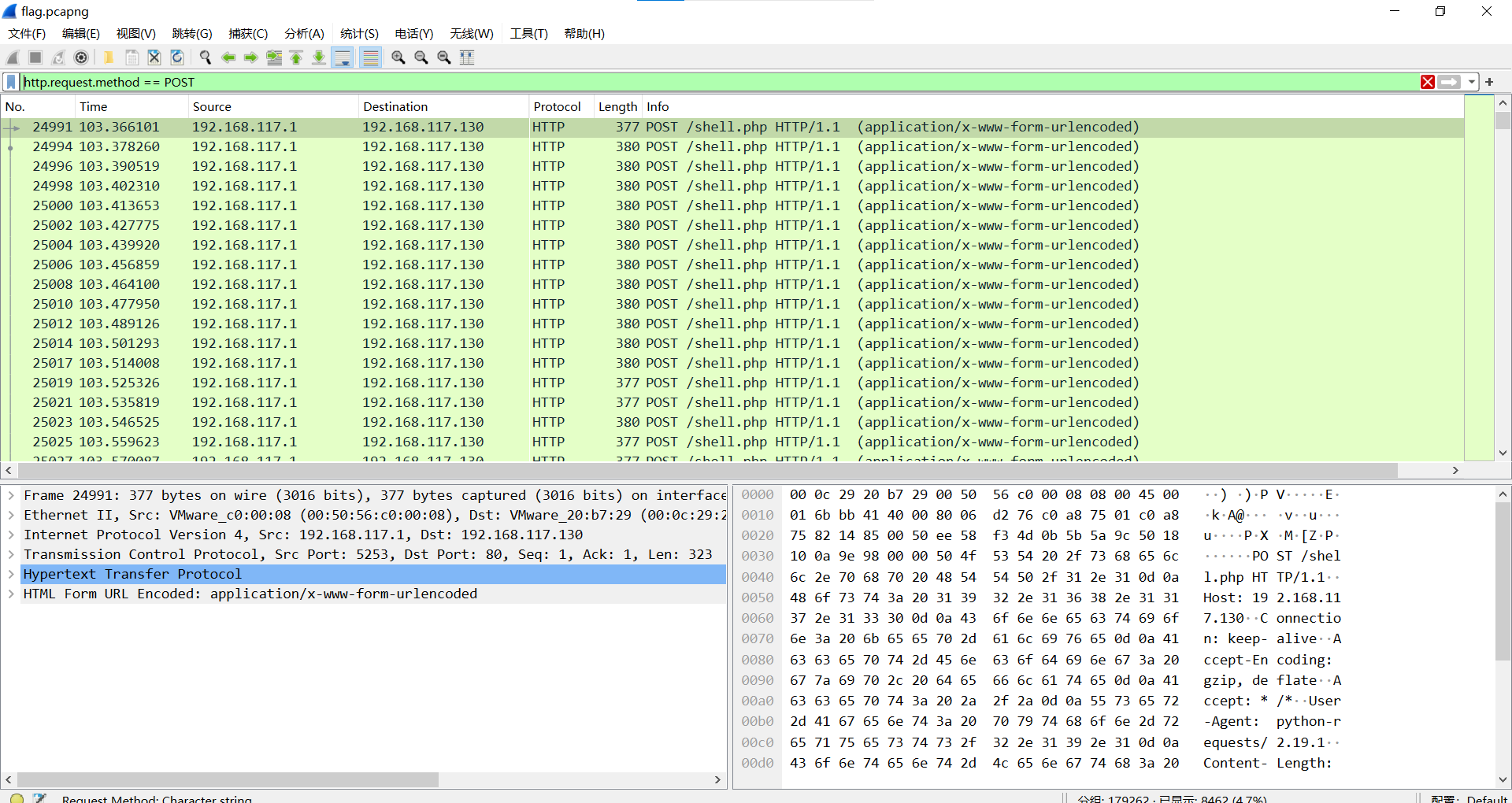
导出特定分组,筛选c38流量文件
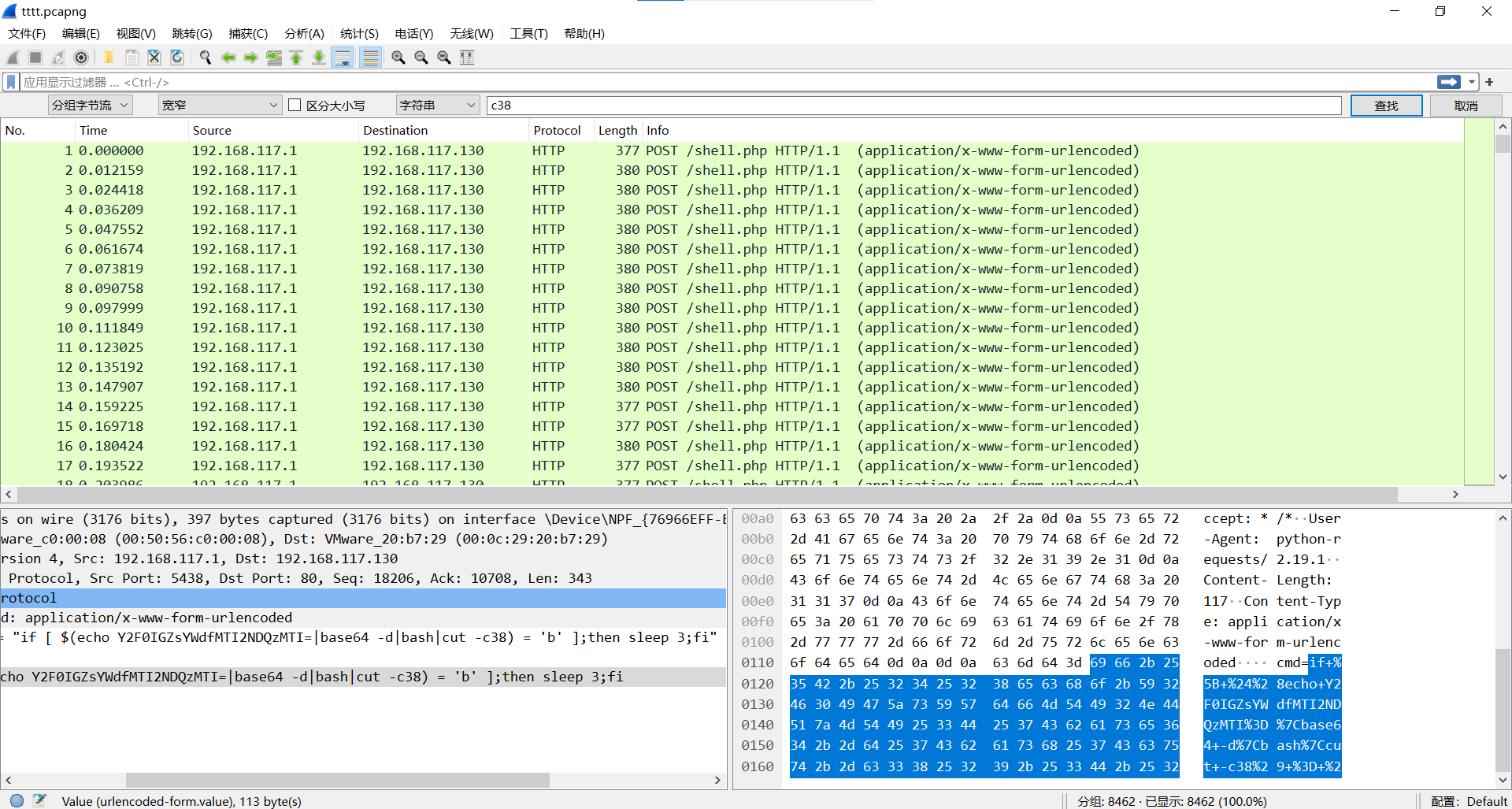
查看文本手撕得到flag
最后flag为flag{3563bd1a59309e1a4e93b65152bfbba}
小刘的硬盘
题目描述:
小刘有一块硬盘误删了一些文件,你能帮帮他么?
下载附件,使用diskgenius挂载磁盘
使用diskgenius恢复文件
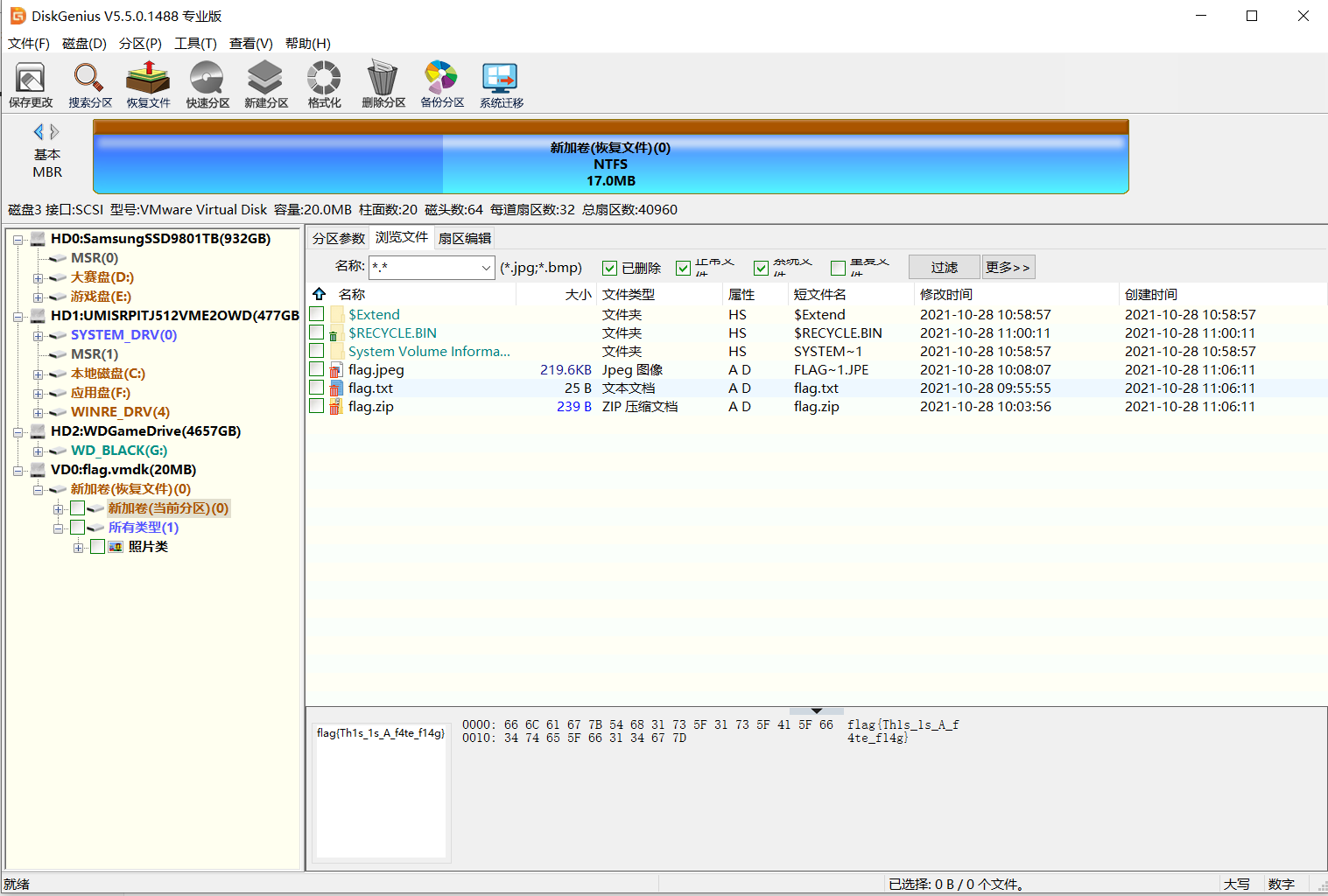
得到一个假flag,一个jpg图片,一个压缩包
jpg文件不存在隐写,考虑压缩包,导出压缩包,发现有密码
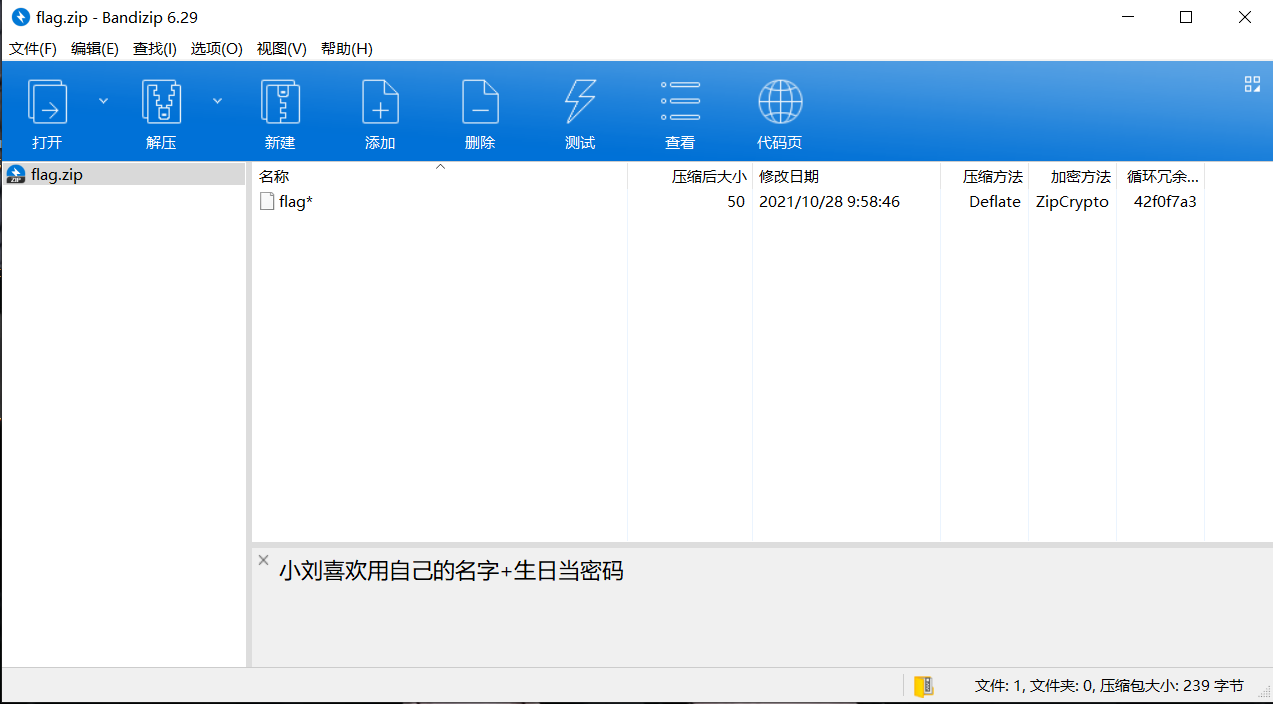
旁边有提示:小刘喜欢用自己的名字+生日当密码
掩码爆破
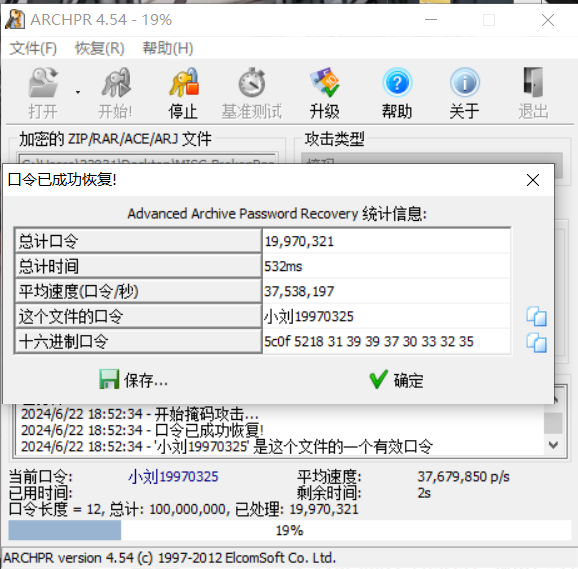
解压压缩包得到flag
最后flag为flag{8ddeed0126f2523ae14a8a492528c9a0}
考古2.0
下载附件
内存取证(vol)
vol.py -f 考古 –profile=WinXPSP2x86 cmdline
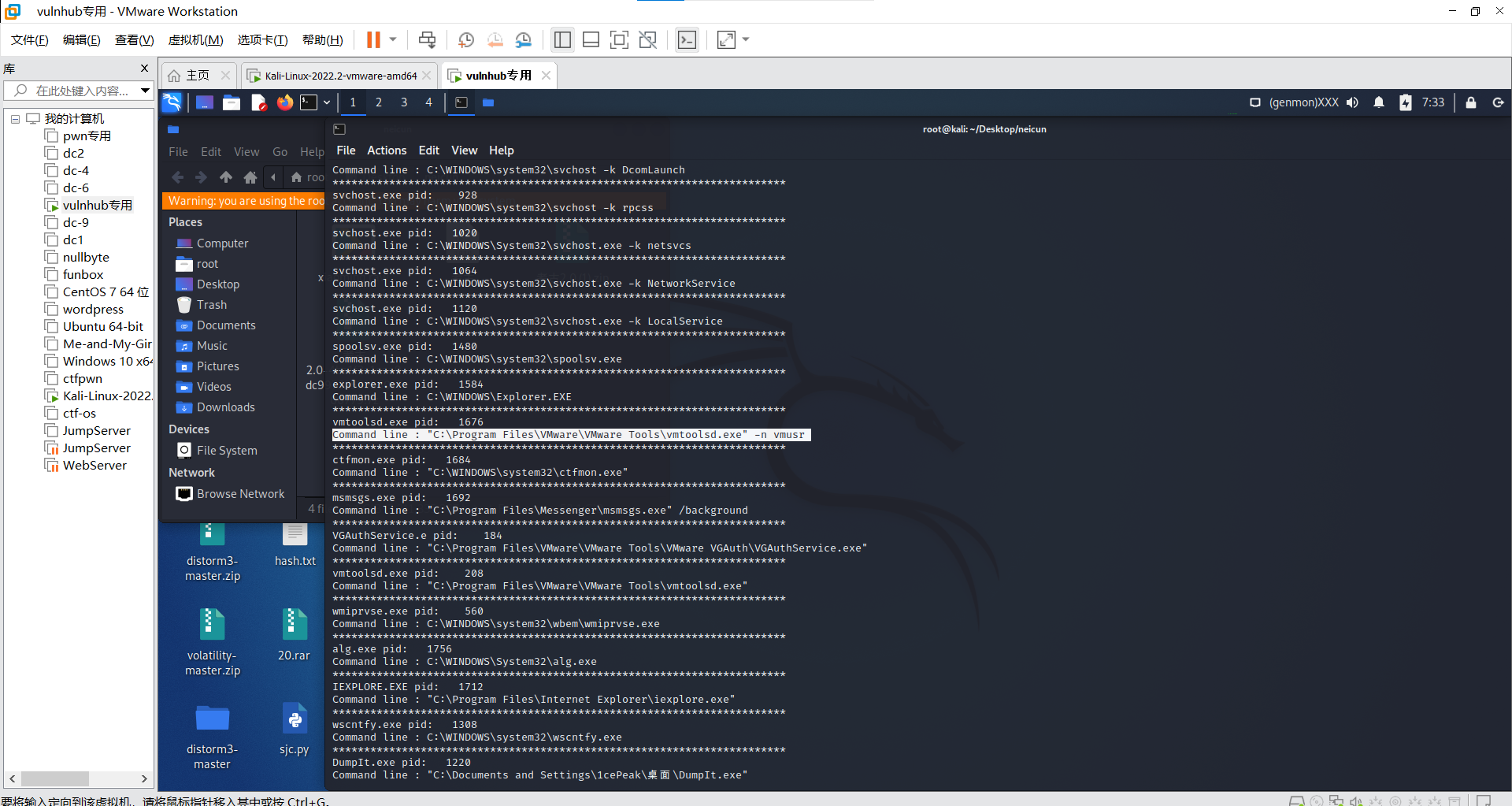
发现virus,搜索文件
vol.py -f 考古 –profile=WinXPSP2x86 filescan | grep virus
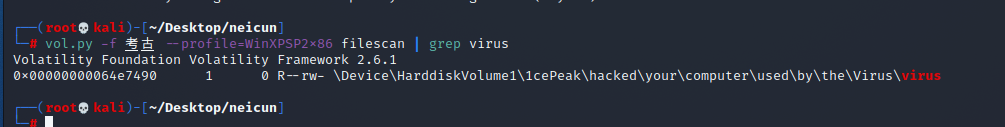
提取文件
vol.py -f 考古 –profile=WinXPSP2x86 dumpfiles -Q 0x00000000064e7490 -D ./
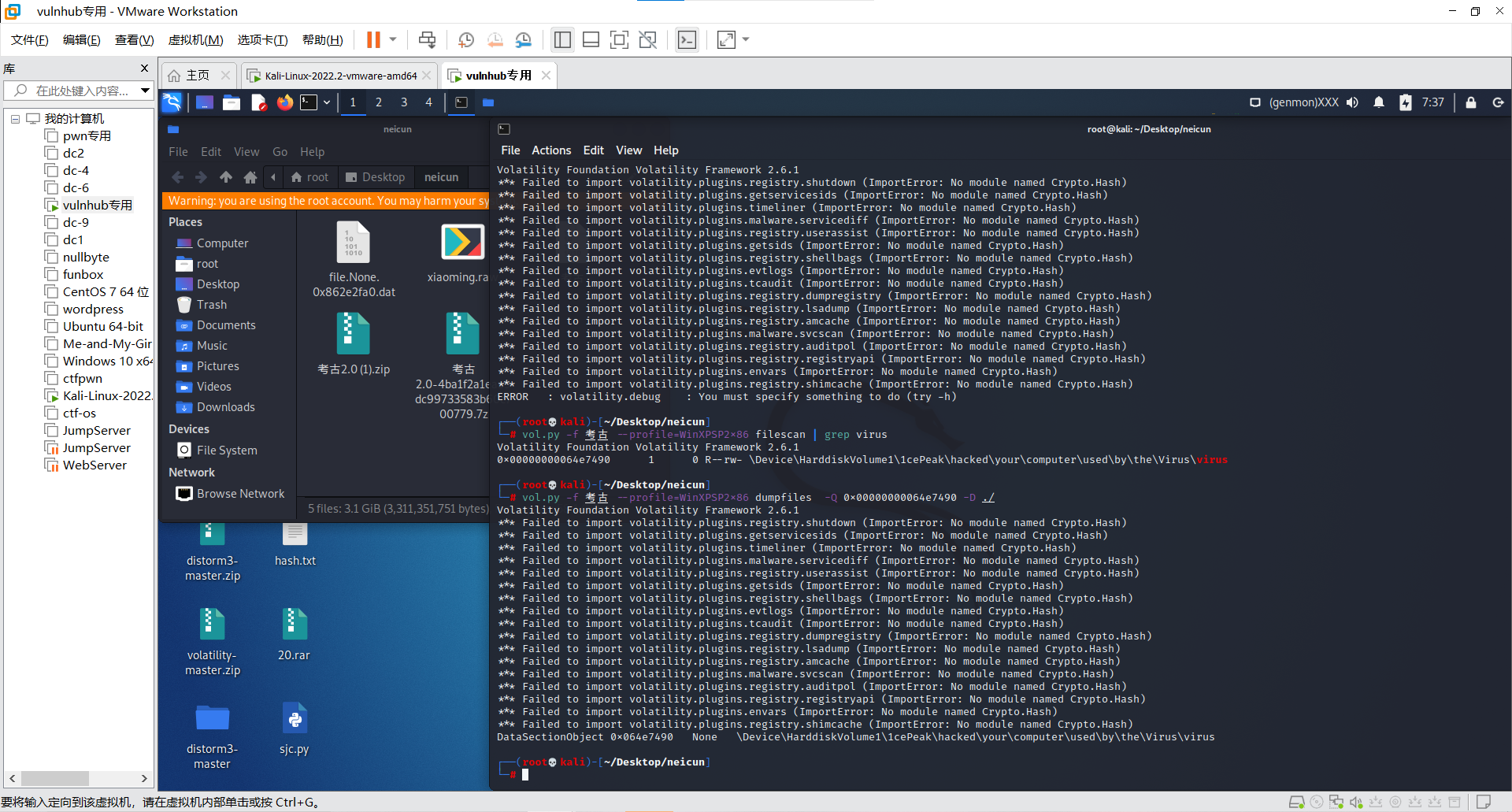
强制异或
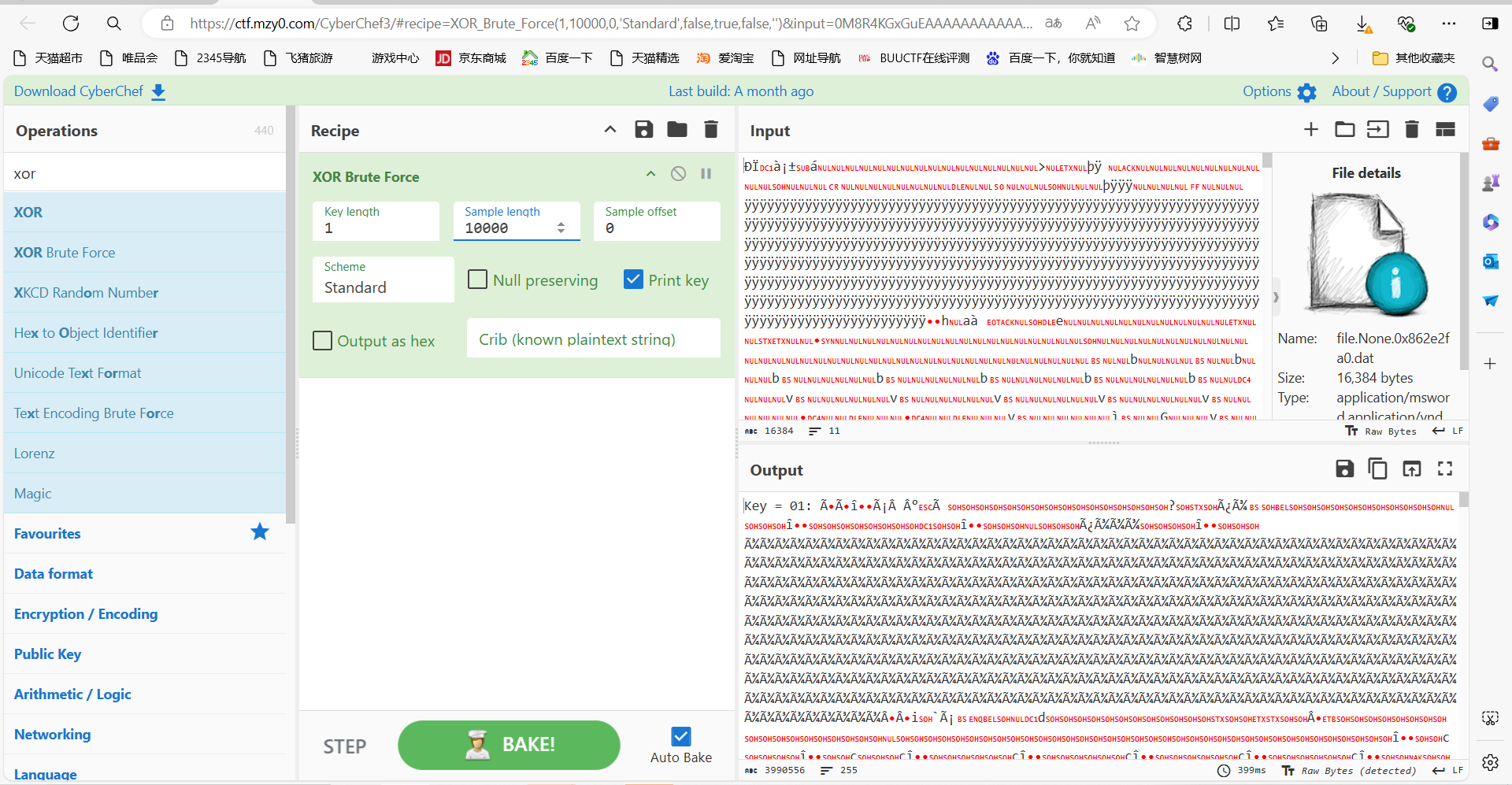
导出,搜索关键字flag
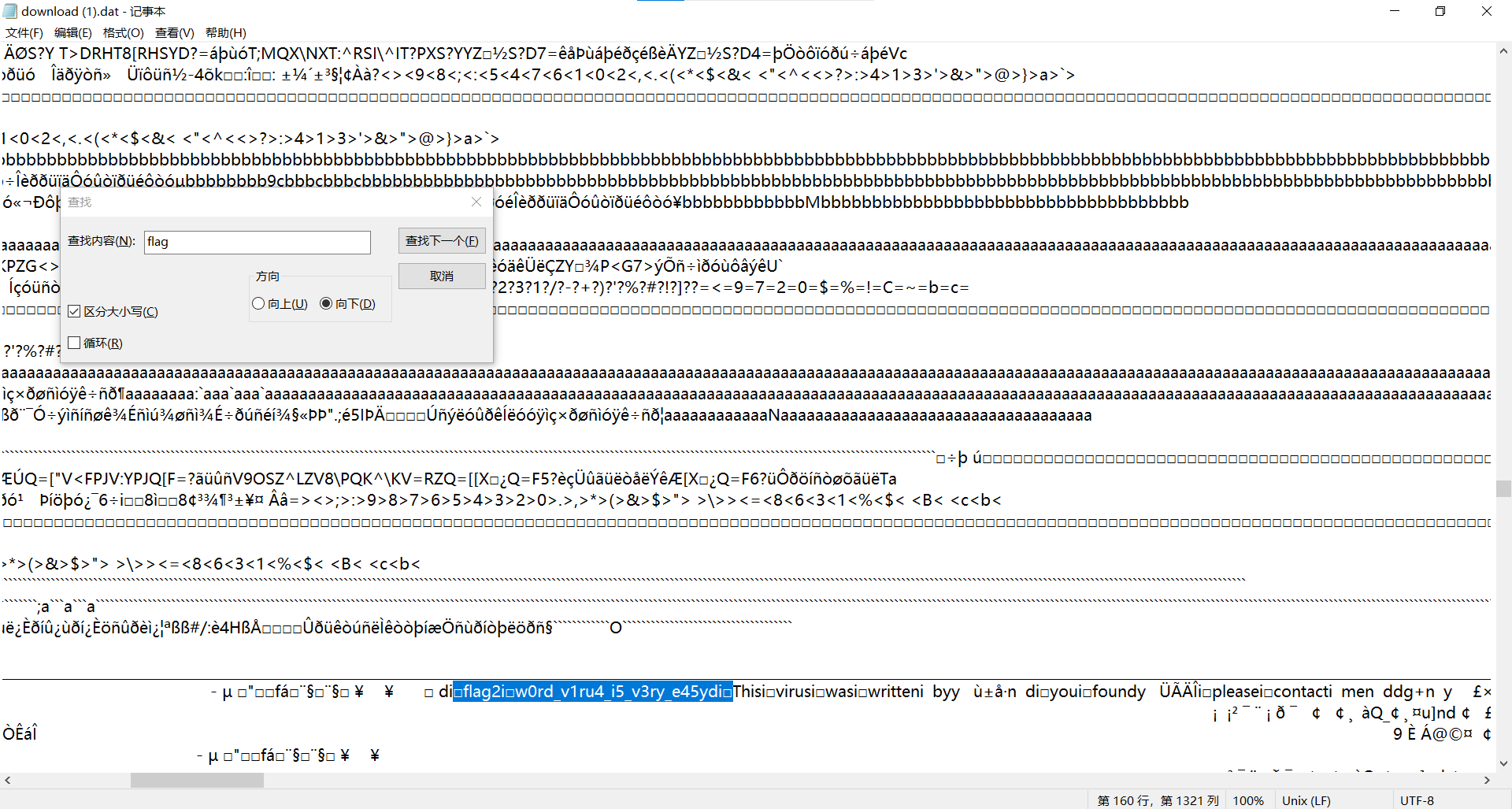
最后flag为flag{w0rd_v1ru4_i5_v3ry_e45y}
Crypto
easyRSA
题目描述:
简单的RSA,你能做出来吗?
题目源码
1 | from Crypto.Util.number import getPrime,bytes_to_long |
中国剩余定理+coppersmith
先通过CRT求出p_2
1 | from Crypto.Util.number import * |
得到p_2
1 | (mpz(157397749849472741302651922559110947585741898399548366071672772026799823577871183957882637829089669634665699886533302712057712796808672023827078956556745522749244570015492585747076324258912525658578733402979835176037760966294532155059241756382643278063578661030876735794467422919824463419065126688059515994112), 115343256339804438488541860602807499768350592243111732022419431132087583829952557330993478731619075521301706171847716910739807488266701790937805652553244788024534230754162298101105496772540567818850570512144853594488579606954797182360716688344137783051055690460297099575344944650143959946929880492674974780957995559861235099499367407389543136733028684627735422306472504011232051138891022767098404805311381687759832357323075065923241564165806258181141497530683119) |
然后再梭个coppersmith
1 | p_high=157397749849472741302651922559110947585741898399548366071672772026799823577871183957882637829089669634665699886533302712057712796808672023827078956556745522749244570015492585747076324258912525658578733402979835176037760966294532155059241756382643278063578661030876735794467422919824463419065126688059515994112 |
1 | #n = 23074300182218382842779838577755109134388231150042184365611196591882774842971145020868462509225850035185591216330538437377664511529214453059884932721754946462163672971091954096063580346591058058915705177143170741930264725419790244574761160599364476900422586525460981150535489695841064696962982002670256800489965431894477338710190086446895596651842542202922745215496409772520899845435760416159521297579623368414347408762466625792978844177386450506030983725234361868749543549687052221290158286459657697717436496769811720945731143244062649181615815707417418929020541958587698982776940334577355474770096580775243142909913 |
最后正常解RSA
1 | import gmpy2 |
运行得到flag
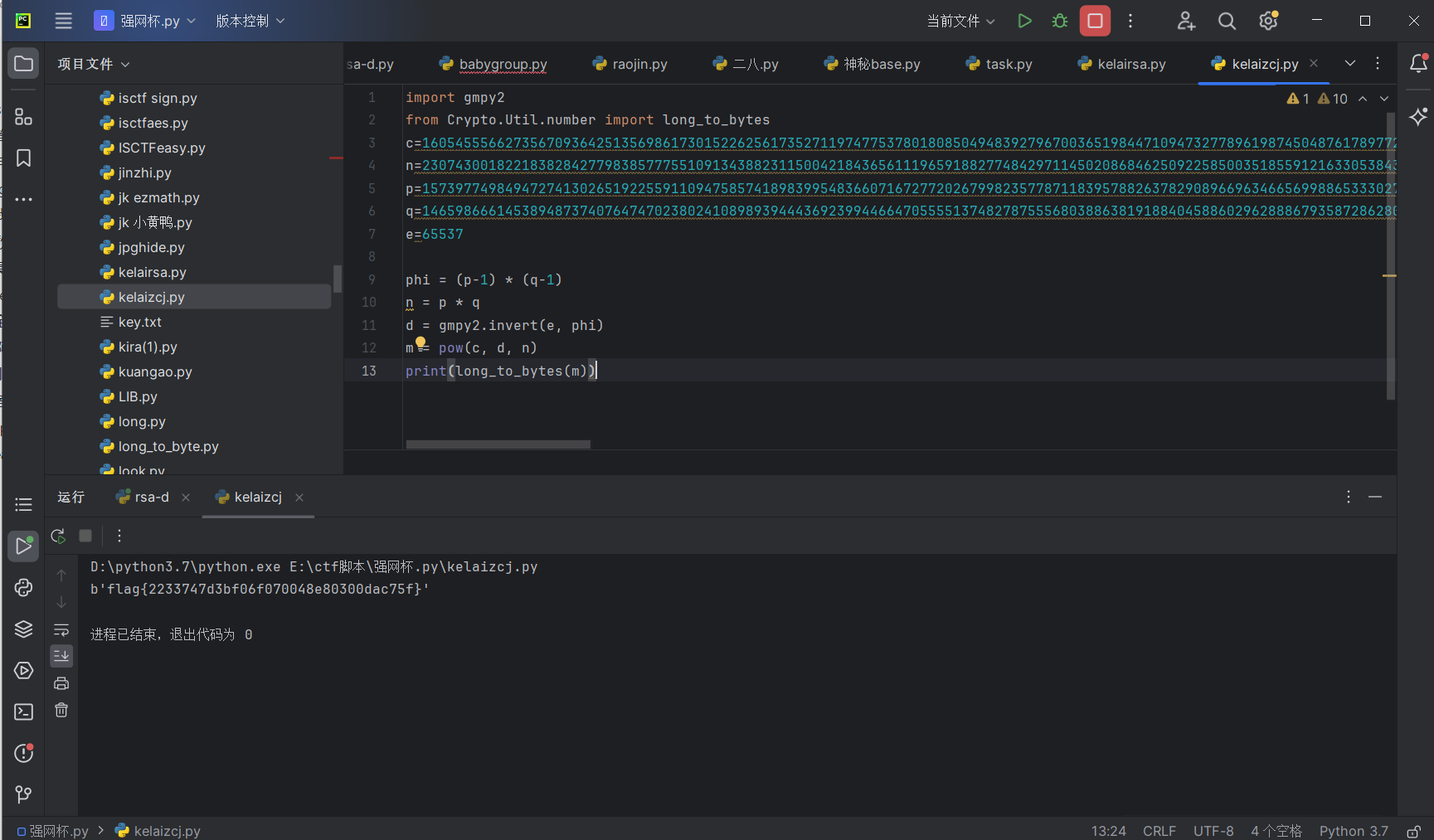
最后flag为flag{2233747d3bf06f070048e80300dac75f}
小试牛刀
题目描述:
一个很简单的密码学题目
题目
1 | ipfm\x82Kj]p~l?\x82ogw\x85mt[K\x8br\x97 |
变异凯撒
exp:
1 | from Crypto.Util.number import * |
运行得到flag
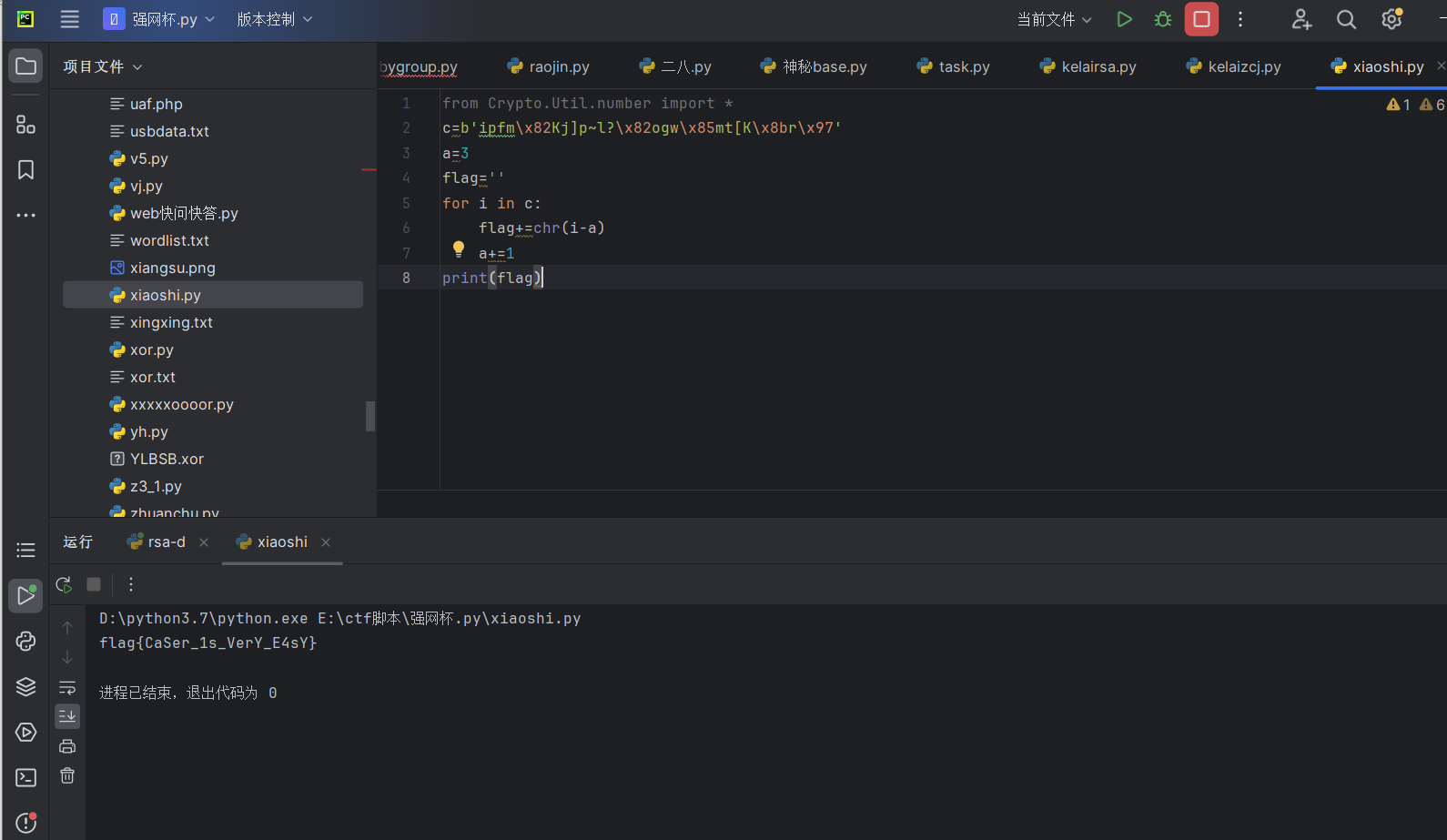
最后flag为flag{CaSer_1s_VerY_E4sY}
Reverse
人生模拟
查壳
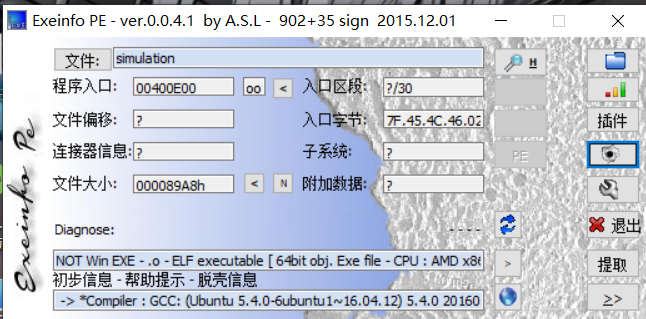
ida64载入
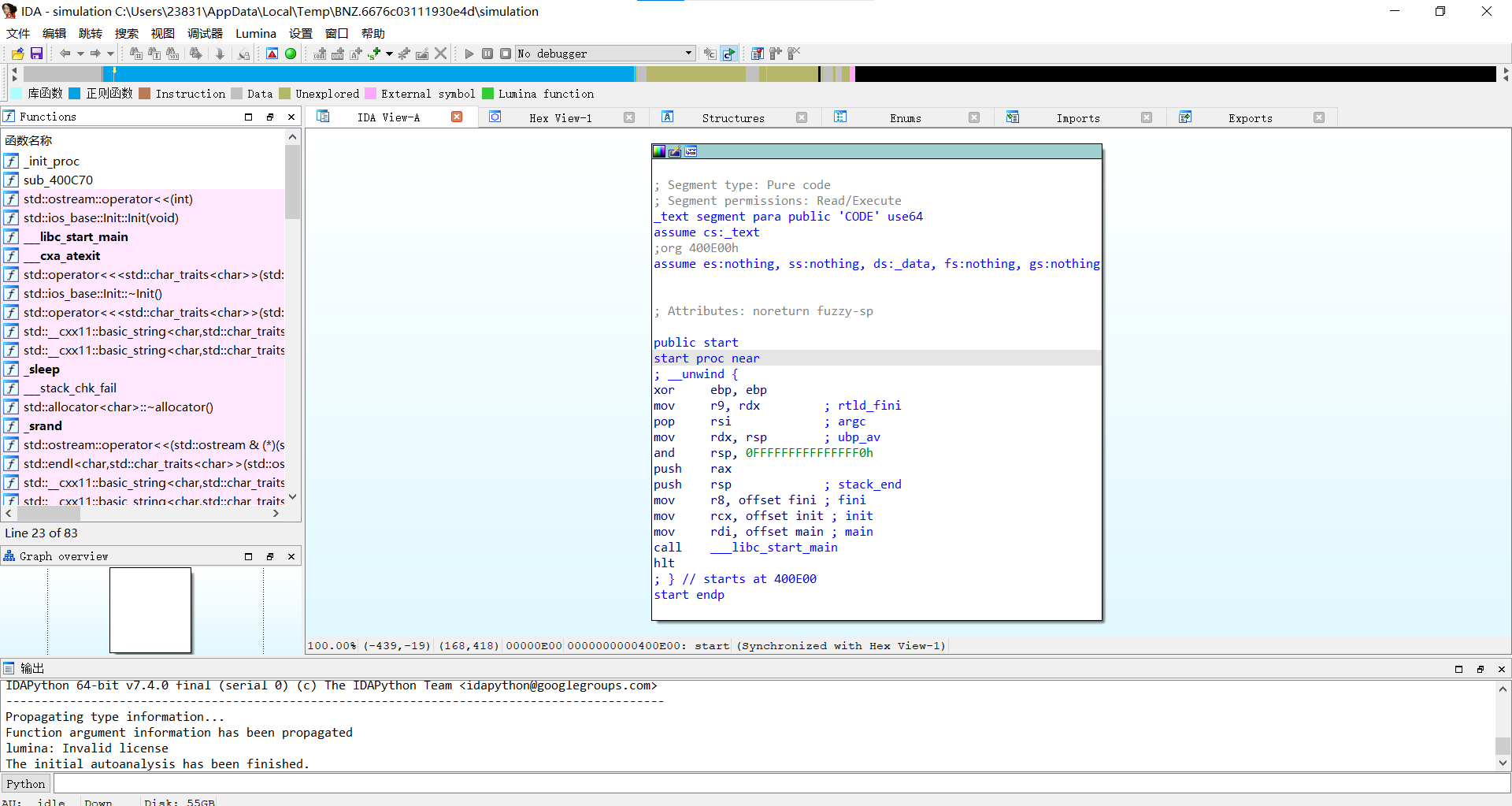
查看关键代码
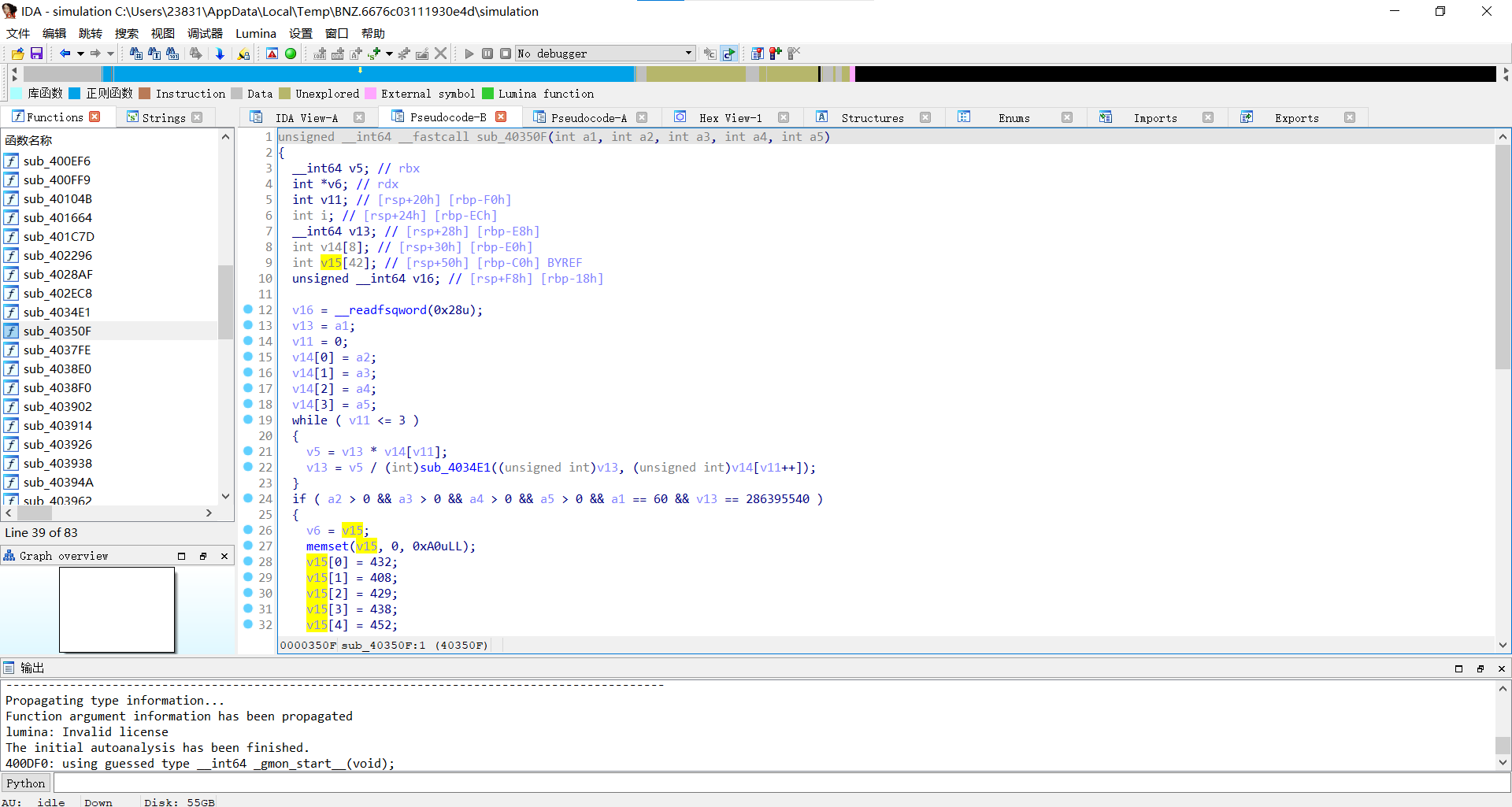
完整代码:
1 | unsigned __int64 __fastcall sub_40350F(int a1, int a2, int a3, int a4, int a5) |
跟着这个加密代码写出解密脚本:
1 | v15=[0]*38 |
运行得到flag